DoH and DoT proxy servers for DNS requests encryption
As we know, the DNS (Domain Name System) protocol does not encrypt requests, and data is transmitted openly. DNS traffic is vulnerable to cybercriminals as there is an opportunity to 'eavesdrop' on the communication channel and intercept unprotected personal data. ISPs can monitor traffic and collect data about what sites you visit.
Special DNS protocol extensions, DNS over TLS (DNS over TLS, or DoT, RFC7858) and DNS over HTTPS (DNS over HTTPS, or DoH, RFC8484) are developed to ensure the security of DNS traffic. Their main purpose is to encrypt DNS traffic to prevent interception and provide additional privacy and security. We won't cover the theory in detail in this article. Information on how DoT and DoH work can be found on the following pages:
There are also lists of public DNS services that support DoT/DoH:
Starting with version 3.0, KeeneticOS supports DNS over TLS and DNS over HTTPS protocols. Below, we will guide you to encrypt your DNS traffic, as sent over the router, by default.
Importante
When the DoT/DoH protocol is enabled, all incoming DNS queries will be sent to the server address specified during the configuration. The DNS servers received from your ISP and/or manually registered DNS servers will not be used.
When AdGuard DNS or Cloudflare Internet safety services are enabled, only the DNS queries from devices that are not registered to use the filter profile (that is, from devices which are using a 'No filtering' profile) will be sent to specified DoT/DoH servers over an encrypted connection.
If you want to use DNS over TLS only, then the 'DNS-over-HTTPS proxy' component should be removed. Same for DNS over HTTPS, remove the 'DNS-over-TLS' component.
Let's show an example of configuration via the web interface. We will use Cloudflare's free DNS service, which supports DoT/DoH protocols.
For the DoT/DoH protocol to work, system components: 'DNS-over-TLS proxy' and 'DNS-over-HTTPS proxy' are needed to be installed. Please open 'System component options' menu by clicking on the 'Component options' button in the 'Management - System settings' section and mark the required components for installation.
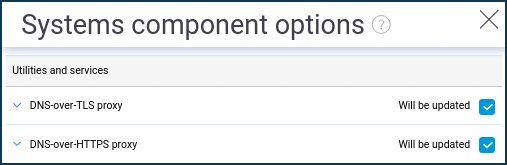
Proceeding then with the setup on the 'Internet safety' page under the 'Network rules' menu section. Navigate to 'DNS configuration' tab.
DNS-over-TLS
Click the 'Add server' link at the bottom of the page.
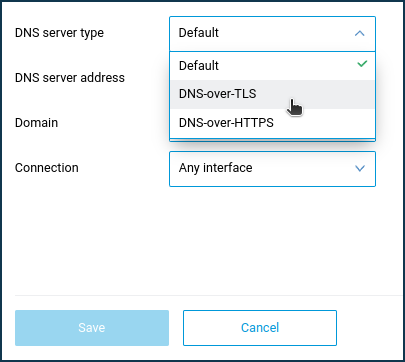
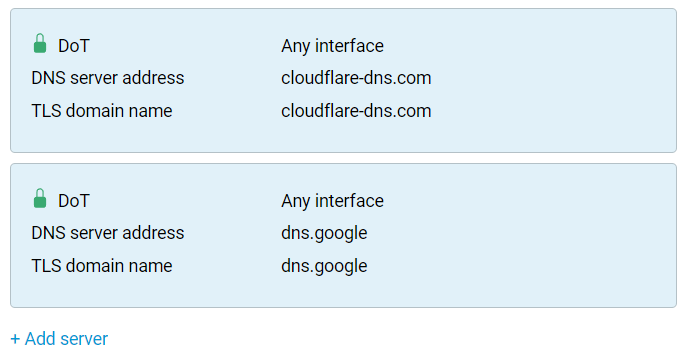
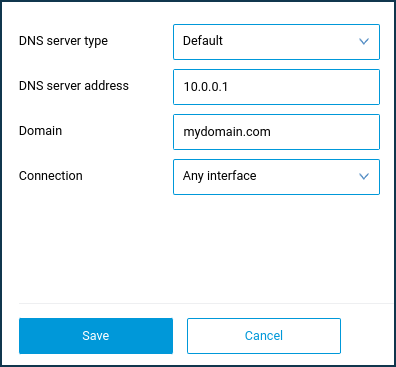
The fields for filling in the server parameters will appear. Specify the DNS server address (in our example 1.1.1.1 and 1.0.0.1), the TLS domain name (in our example cloudflare-dns.com), and, if necessary, the Connection interface (the default setting is 'Any interface').
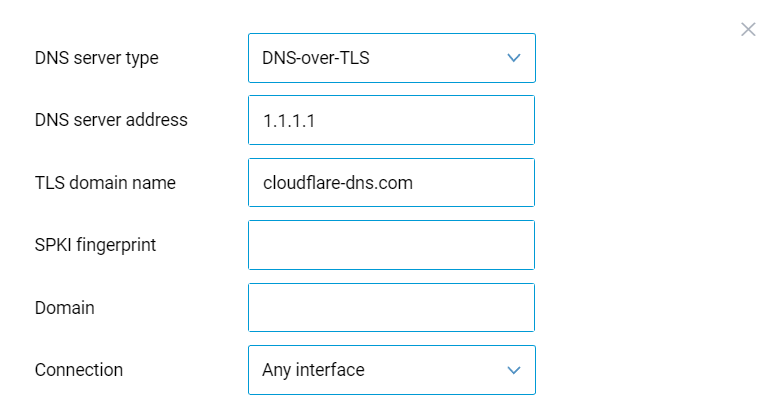
For example:
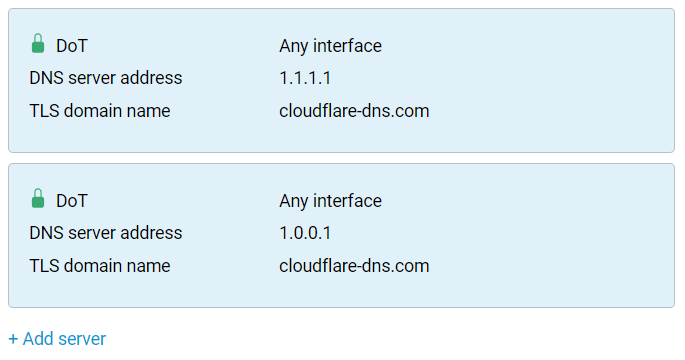
In the 'DNS server address' field, it is allowed to specify the FQDN domain name, e.g.:
Importante
For DNS resolving to work stable, multiple DoT/DoH servers must be specified simultaneously, preferably from different DNS services. For example:
DNS server address | TLS domain name |
|---|---|
8.8.8.8 | dns.google |
8.8.4.4 | dns.google |
1.1.1.1 | cloudflare-dns.com |
1.0.0.1 | cloudflare-dns.com |
9.9.9.9 | dns.quad9.net |
94.140.14.14 | dns.adguard-dns.com |
94.140.15.15 | dns.adguard-dns.com |
DNS-over-HTTPS
Click the 'Add server' link at the bottom of the 'DNS Configuration' tab.
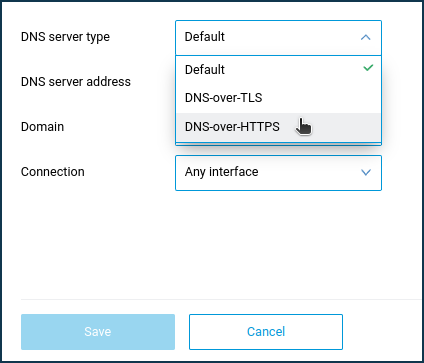
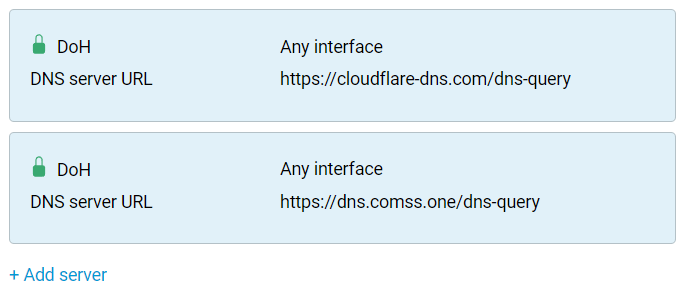
Fields to fill in specific parameters will appear. In the 'DNS server type' field, specify 'DNS-over-HTTPS', in the 'DNS server address' field, specify the name of the DNS server and, if necessary, specify the connection interface (the default setting is 'Any interface'). These queries use the DNS message format. In our example, the https://cloudflare-dns.com/dns-query and https://dns.comss.one/dns-query servers are added.
For example:
Nota
When multiple DNS-over-TLS and/or DNS-over-HTTPS servers are specified in the router settings, the system resolver will use them in the order of priority on the measured response time.
A maximum of 8 DoT/DoH servers can be used in Keenetic routers.
Checking the settings
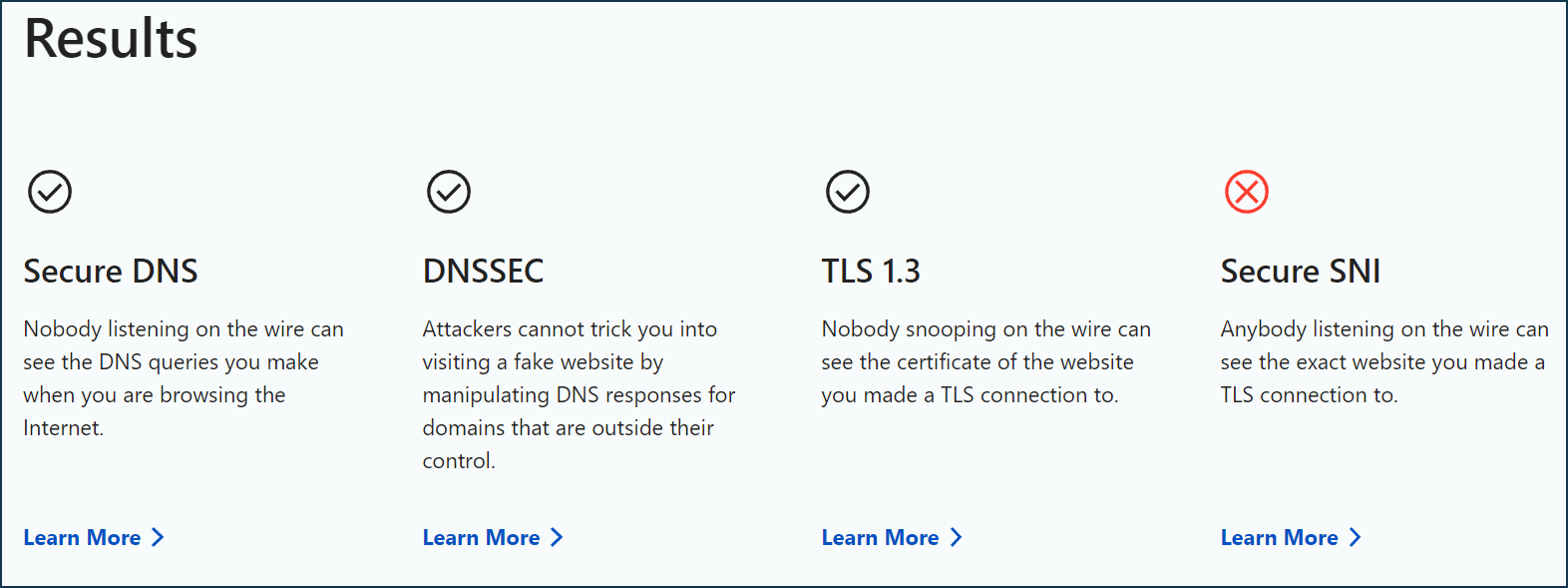
The Cloudflare service also supplies verification pages. Let's open a special webpage at the address https://www.cloudflare.com/ssl/encrypted-sni/ to check the browser security.
Click the 'Check My Browser' button on that page to start the DNS query processing test.
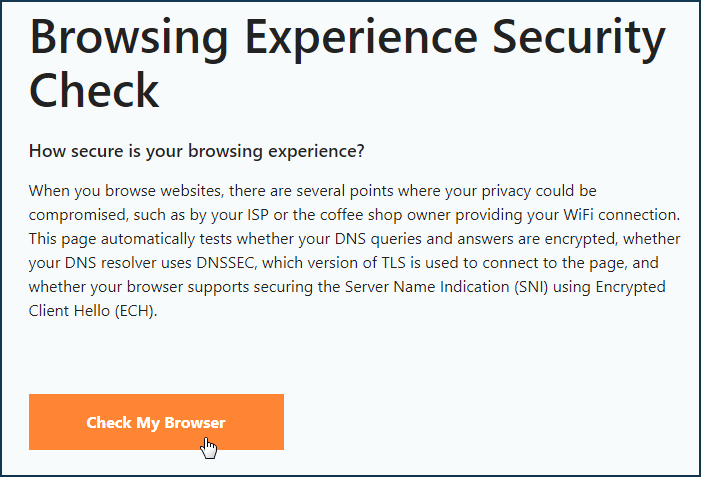
If the above settings are configured correctly, the test should be completed successfully for 'Secure DNS', 'DNSSEC', and 'TLS 1.3'. The correct output of DoT/DoH and browser security checks depends on the availability of DoT/DoH servers/addresses in the ISP/operator network.
Importante
This article shows an example of a DoT/DoH check for the Cloudflare service. The check at https://www.cloudflare.com/ssl/encrypted-sni/ may fail if you use other DNS services. It will also fail if you have specified any DNS addresses in the DHCP settings of your Keenetic home network. Because then the devices connected to Keenetic will contact these DNS servers directly and not to Keenetic with DoT/DoH configured.
To repeat the test, please press the 'Run the test again' button on the page.
If the test failed, it is possible that third-party DNS servers were previously assigned in the IP settings of the network adapter in Windows, Linux, macOS. In this case, all DNS requests will be handled through third-party DNS, and DoT/DoH will not work. Remove the previously specified third-party DNS addresses and retest.
Also, note that if you specify multiple DoT/DoH addresses from different services, the result of the check depends on which server is currently in priority. For example, if the DoH server specified is https://dns.google/dns-query in DNS message format, it will fail the 'Secure DNS' check.
Suggerimento
If you do not want to configure DoT/DoH manually, enable the AdGuard DNS or Cloudflare DNS internet filter. In this case, you will not need to do any additional configuration. When you enable AdGuard DNS or Cloudflare DNS, DoT/DoH support will automatically turn on, but only if the Internet filter has the system components to support DoT/DoH installed. Otherwise, the Internet filter will not use the specified encryption protocols.
You can verify DoT/DoH support through the router's command line interface (CLI) by running
show adguard-dns availabilityorshow cloudflare-dns availability.When AdGuard DNS and Cloudflare DNS are enabled, the service status check on https://adguard.com/en/test.html and https://1.1.1.1/help might not pass.
This is normal, and when Internet filters are enabled, it is set to block the transit DoT/DoH by default to avoid DNS query leaks.
When DoT/DoH proxies are manually specified in Keenetic, and one of the internet filters, Adguard DNS or Cloudflare DNS, is enabled, the internal system domains and internet checks are resolved first via DNS proxies, i.e. manually specified DNS addresses.
To prevent a DNS query from being hijacked, you must specify the domain in the DNS server add settings. For example:
You can check DNS queries for the Cloudflare service by visiting https://www.cloudflare.com/ssl/encrypted-sni/
Click 'Check My Browser' to run the test.

If DoT/DoH is configured correctly, the test should complete successfully for 'Secure DNS', 'DNSSEC' and 'TLS 1.3'. The correct output of the DoT/DoH and browser security test depends on the availability of DoT/DoH servers/addresses in the ISP/mobile operator network.

Importante
This is an example of DoT/DoH validation for Cloudflare. If you use other DNS services, the check on https://www.cloudflare.com/ssl/encrypted-sni/ may fail. It will also fail if any DNS addresses have been specified in the DHCP settings of the Keenetic home network. In this case, the devices connected to Keenetic will address these DNS servers directly, not Keenetic with DoT/DoH configured.
To run the test again, click 'Run the test again'.
If the test fails, it is possible that third-party DNS servers were previously defined in the IP settings of the network adapter in Windows, Linux, and macOS operating systems. In this case, all DNS queries will be processed through third-party DNS, and DoT/DoH will not work. Delete the previously specified third-party DNS addresses and repeat the test.
Also, keep in mind that if you specify multiple DoT/DoH addresses from different services, the result of the test depends on which server is currently in priority. For example, if a DoH server https://dns.google/dns-query is specified in DNS message format, it fails the 'Secure DNS' check.