SSH remote access to the Keenetic command line
The SSH (Secure Shell) server allows securely connecting to the router command line. Now we will see how to configure a device for a remote connection to its command-line interface (CLI).
To run the SSH server, the 'SSH server' system component must be installed in the Keenetic. You can do this on the 'General system settings' page in the 'Component options' section by clicking on the 'Component options'.
Once the component is installed, the SSH server will automatically turn on. It can be accessed in local interfaces with a private security level. For information on the access levels that determine the security level (the firewall logic), see the article Firewall rules configuration from the command interface.
To allow access from external networks, the SSH server must have a 'public' level of security. Run the commands at the router command-line interface:
(config)>ip sshCore::Configurator: Done. (config-ssh)>security-level publicSsh::Manager: Security level changed to public.
To avoid unwanted hacking attempts by bots, random Black/Grey Hat hackers, and in cases where the standard port is already running the SSH server in the OPKG subsystem, it is recommended to change the standard port of the server. The default port on which the server is running is standard port number 22. You can change it to one of the unused numbers (for example, 2022):
(config-ssh)> port 2022
Ssh::Manager: Port changed to 2022. Now users who have access to the Keenetic command line will be able to reach the external IP address of the device on port 2022 from an SSH client and get access to its command line in a secure encrypted channel.
To save the setting, you need to execute the command:
(config)> system configuration save
Core::ConfigurationSaver: Saving configuration...Connecting to an SSH server
To connect to your Keenetic via SSH protocol, you can use any terminal program that supports this type of connection. For example, a free client, PuTTY.
Download, install and launch the PuTTY terminal client on your computer. Specify the connection type 'SSH' in the 'Connection type' field. Enter in the 'Host Name or IP address' field the network name or IP address of the device (local IP when connecting from a home network or public WAN IP when connecting from the Internet), and in the 'Port' field — the port number by which the connection will be established (by default SSH protocol uses port 22, in our example port 2022 is used).
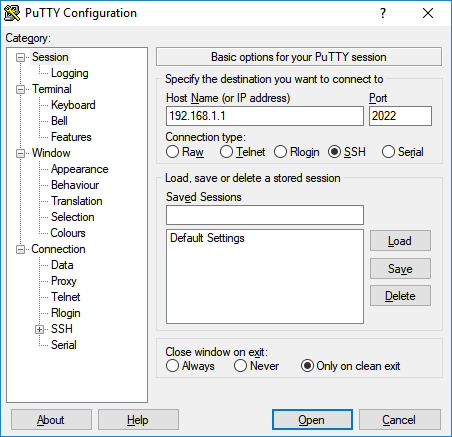
After clicking the 'Open' button, you will be prompted for the login and password to authenticate on the device. Enter the administrator account credentials. After successful entry of the administrator login and password, the router command line will appear.
It is also easy to establish an SSH connection from Linux. For example, to connect an SSH client with the admin username, you should use the command:
[alexander@silverado ~]$ ssh admin@192.168.1.1 -p 2022
Warning: Permanently added '[192.168.1.1]:2022' (ECDSA) to the list of known hosts.
admin@192.168.1.1's password:
X11 forwarding request failed on channel 0
(config)> If your keys are compromised, the SSH server can generate new keys. This procedure automatically occurs when you install the system component, but can also be started by ip ssh keygen {keygen} command, where instead of {keygen} you should specify the required algorithm — default for example.
(config-ssh)> keygen default
Ssh::Manager: Key generation is in progress...
progress, name = SSH key generation: 0
....
progress, name = SSH key generation: 50
progress, name = SSH key generation: 100 If you have changed the keys on the server, you should clean them up on the client that remembers them automatically. In Linux, you can use the ssh-keygen application with -R key to do this (case is sensitive because -r key is used to print the saved key hash values to the screen):
[alexander@silverado ~]$ ssh-keygen -R '[192.168.1.1]:2022'
# Host [192.168.1.1]:2022 found: line 1
/home/alexander/.ssh/known_hosts updated.
Original contents retained as /home/alexander/.ssh/known_hosts.oldNota
Starting with KeeneticOS 2.11, unprotected telnet sessions of router management via the command line are automatically terminated after 3 minutes of user inactivity. This timeout value can be controlled, but it is impossible to set an infinite duration of the session.
The default timeout of 300 seconds (5 minutes) is set for the SSH connection session. If necessary, this value can be increased. This parameter can be set to 232-1 seconds inclusively.