How does a firewall work?
A firewall is designed to protect local network devices from external attacks. By default, all home network computers are hidden from Internet users by a built-in firewall and NAT network address translator.
NAT network address translation mechanism masks the addresses of LAN computers behind a single address of the external interface. It works directly with the frame content, substituting the source and destination addresses.
A firewall interacts with traffic after the address translation and routing and controls and filters traffic according to the specified rules based on IP addresses.
The router's built-in firewall allows connections from home interfaces (LANs) to public networks (WANs) and prohibits them in the opposite direction. Custom settings can be used to change security options: allow or deny access to specific hosts or network services.
By default, the interface designed to connect to external networks or access the Internet is public (external). For example, such interfaces are:
dedicated Ethernet connection;
wireless connection via a 3G/4G/LTE mobile Internet USB modem;
connection with authentication based on PPPoE/PPTP/L2TP protocols.
Private (local, home) are home network interfaces (clients connected to Keenetic device via Ethernet and Wi-Fi) and guest wireless network interfaces.
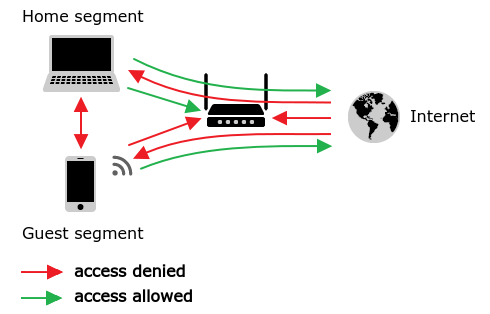
By default, a Keenetic router accepts network connections from private interfaces only. From private interfaces, it is allowed to establish connections to public interfaces and the device itself for management and access to services enabled on the router (FTP, Transmission, network use of USB). For clients of the guest network, access to the router and its services is denied.
The connection between private interfaces is not allowed by default, but access can be granted if necessary.
It is forbidden to establish connections to any other interfaces and the device itself from public interfaces.
Important
By default, access to the device management (web interface) from the external network is blocked.
1. How is the firewall implemented?
To simplify, a firewall can be represented as a set of pre-configured and user-defined filters, where user-defined rules have higher execution priority.
The firewall operates with the following settings:
IP parameters (basic criteria of filtering rules): IP address/Subnet, Protocol, Port number;
the actions of these rules (Deny or Allow) on network traffic packets;
binding rules to a specific interface.
The user part of the Keenetic firewall implements filtering rules created for a specific interface. When creating a firewall rule, it is very important to correctly define the interface for which it will be made. The fact is that the binding of rules to the interface also defines the direction of traffic flow to which these rules will be applied. Rules can be executed for incoming or outgoing traffic of a WAN or LAN interface.
Incoming direction (in) — always to the device, outgoing (out) — from it.
Regarding the interface, the flow direction is defined as:
incoming direction (in) for traffic from the external network to the local one on a WAN port, for LAN interfaces, this direction is outgoing (out);
the flow from the local network to the external one for WAN interfaces is outgoing (out), and for LAN interfaces incoming (in).
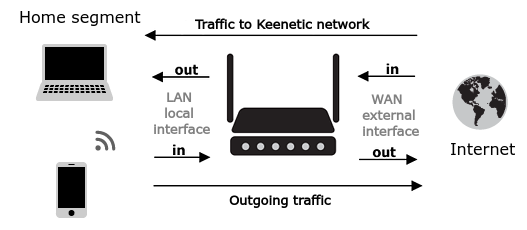
According to the given scheme, an incoming packet from the external network to the local one on the WAN interface has an incoming direction for a firewall rule. Still, on the LAN interface, a rule to control this traffic is outgoing (out).
Important
In Keenetic routers, firewall rules are not 'packet-based', but are applied within a session (connection). Therefore, when blocking access to somewhere, you need to prohibit the packets movement from the initiator of the request rather than the answers to these requests. For example, to deny access via HTTP from local hosts to the external address 77.88.99.10, you need to create one rule on the local LAN interface because the session initiator (incoming traffic) is on the local network.
It should also be noted that if a session has already been installed, and after that, the configuration of the firewall rule is applied to the traffic in this session; this existing session will not be controlled by the firewall. The rule will take effect after the current session is terminated — forced or at the end of the session lifetime.
For the newly created rule to work correctly (to reset current/active connections), the interface to which it applies should be disabled and enabled again.
2. Configuring firewall rules
The firewall rules are executed in the order they are specified in the list: the top one first and then further down. For any rule (actually, for any group of rules or Access Control List), the interface on which they will be executed must be defined.
Each rule should specify:
a network of traffic source and destination (IP addresses of hosts or subnets);
a protocol for the configuration (TCP, UDP, ICMP);
a port number for TCP and UDP protocols is required;
an action to be performed on a packet: deny or permit.
Important
In Keenetic devices, firewall rules are processed after Network Address Translation (NAT) rules. Therefore, when creating firewall rules, it is necessary to specify the host's IP address after the address translation.
3. Configuring rules from the web interface
The router web interface provides the most comfortable way to manage firewall rules. But there is a limitation: rules created through the web interface apply only to the incoming (in) direction. You cannot configure rules for outgoing (out) direction. It is possible to create rules for any direction via the сommand-line interface (CLI) of a Keenetic router.
Firewall rules are set up on the 'Firewall' page. When you add or edit a rule, you select the 'Permit' or 'Deny' action in the 'Settings' window, and specify the criteria-conditions when these actions will be performed.
Tip
Rules should be created for the interface where the filtered traffic initiates the session;
When creating rejection filters, the permit rules must be placed above the deny rules;
When setting up rules, you can use IP addresses only (you cannot use domain names when specifying the source or destination address).
For information on configuring firewall rules from the web interface, refer to the Firewall instruction.
4. Firewall exceptions
Some applications (services) in Keenetic routers change security policies for their work by themselves. These include, for example, VPN and FTP servers, setting up port forwarding in NAT from an external interface to a computer in the local network or UPnP service (a mechanism that automatically opens ports to hosts in the local network). No additional settings are required from a user, and the necessary permissions are added automatically (for example, when configuring port forwarding in NAT, you do not need to create additional rules in the firewall, permissions for access are created automatically).
But if necessary, you can use custom rules to limit the traffic that comes through the automatically opened paths, leaving only the required one. The general logic of such limitations is 'allow what you need, prohibit everything else'.
For example, an enabled PPTP VPN server automatically opens incoming port TCP/1723 on each active device interface. If you need to restrict connections from specific addresses on the Internet, on the external interface, you should create rules that allow the TCP protocol on the destination port 1723 from the necessary source addresses and then — prohibit the TCP protocol on port 1723 from any other hosts.
You can configure firewall rules from the command line interface (CLI) of Keenetic.
For more information, see the article: Firewall rules configuration using the command-line interface.
Tip
We recommend reading the 'Firewall rules examples' manual.