OpenVPN client
OpenVPN is one of the most popular protocols for VPN connections. It can be used to create a virtual private network or to interconnect local networks. OpenVPN is open source and distributed free of charge under the GNU GPL license. It provides faster connection speeds than other VPN protocols. Also, OpenVPN can be called one of the safest protocols. All transmitted data is securely protected by the OpenSSL encryption library and SSLv3/TLSv1 protocols, which provides high security and anonymity.
OpenVPN client and server support is integrated into Keenetic routers. To configure an OpenVPN connection, it is necessary to install the 'OpenVPN client and server' system component. A Keenetic router can be used both as a client and as an OpenVPN server with this component. A detailed description of the server mode can be found in the article 'OpenVPN server'. You can install the system component on the 'General system settings' page in the 'Updates and component options' section by clicking 'Component options'.
Важливо
Keenetic routers use strict OpenVPN configuration requirements. Below are some basic requirements:
The configuration must be in a single file.
Certificates, keys, etc., should be included in this file.
Configuration files with the .ovpn extension are usually compatible.
If the ISP offers files for different routers or systems, in most cases, you can use a file for OpenWRT.
In the configuration, you should use only the options listed in the document: https://community.openvpn.net/openvpn/wiki/Openvpn24ManPage
There should be no directives or unknown commands in the configuration that cannot be processed.
Some of the options described above may not be supported. For example, our OpenVPN implementation does not support options related to IPv6.
The order of the options, enabled certificates, and keys do not matter.
The OpenVPN configuration file is not saved in the
startup-configconfiguration file. To get a backup of the OpenVPN client interface settings, you must save it separately.
The number of client connections is limited by the allocated service memory partition size of 24 Kbytes for storing VPN configurations. This is especially important for OpenVPN connections because the total size of their configurations must not exceed 24 Kbytes.
VPN providers can offer different variants for OpenVPN configurations. Below we will review some of them.
Download the configuration file from the site of the OpenVPN server you plan to connect to.
For example, on www.vpngate.net, select the server and click on 'OpenVPN Config file'.
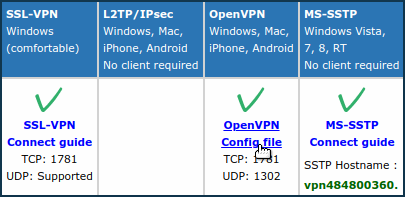
Next, select one of the configurations of this server, for example, with the DDNS domain name and
TCP 1781.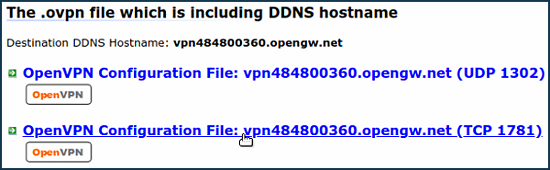
The configuration file with the
.ovpnextension will be downloaded to your computer. Open it in any text editor (e.g. Notepad) and copy all the contents to the clipboard by pressingCtrl-Aand thenCtrl-Ckeys on the keyboard.After that, go to the 'Other connections' page and click 'Create connection' in the 'VPN Connections' section. In the 'VPN Connection Settings' window, select 'OpenVPN' in the 'Type (protocol)' field.
Then enter the name of the connection in the field 'Connection name' and in the field 'OpenVPN configuration' insert the copied configuration from the clipboard by pressing
Ctrl-V. Save the settings.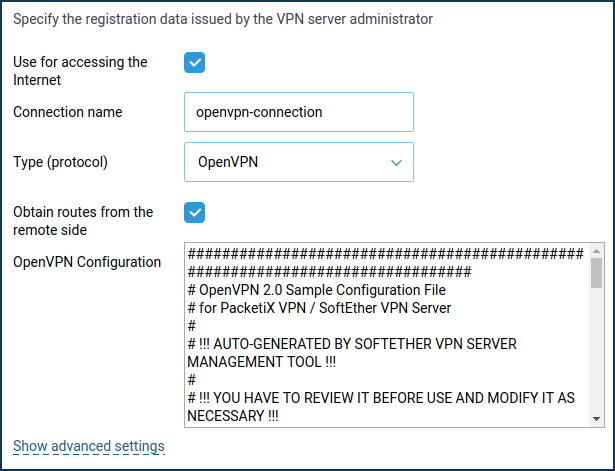
To set up a work schedule or define the interface through which the connection will work, click on 'Show advanced settings'.
Once the connection is established, put the switch in the 'On' state.The status of the connection will also be displayed on this page.
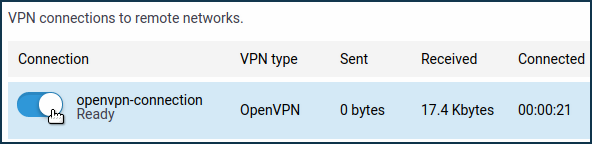
Підказка
If you want to use this connection for accessing the Internet, assign the highest priority to it. You will find information about the priorities in the 'Connection priorities' article.
On some sites with OpenVPN settings, in addition to the configuration file, there is a
loginandpasswordspecified. For example, on vpnbook.com.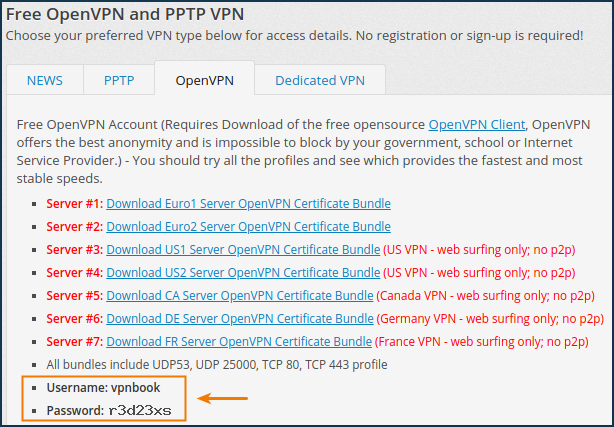
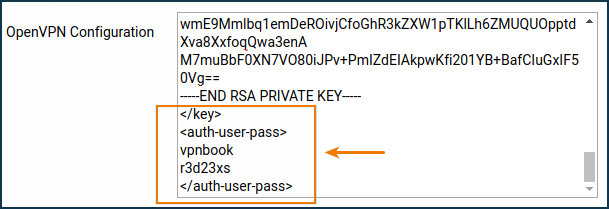
In this case, before copying the content from the configuration file to the clipboard, it is necessary to delete the line:
auth-user-pass
and add a section by entering the required
loginandpasswordvalues. For example:<auth-user-pass> vpnbook r3d23xs </auth-user-pass>
Other ISPs, such as altvpn.com, provide certificates and keys as separate files. In this case, you need to:
Comment out the lines with the certificate and key file names with the symbol
#:#ca ca.crt #cert xxxxxxxxxxxx.crt #key xxxxxxxxxxxx.crt
At the end of the configuration file, add the certificate and key sections and insert the contents of the corresponding files:
<ca> -----BEGIN CERTIFICATE----- ... <--insert the body of the certificate from the ca.crt file here -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- ... <--insert the body of the certificate from the xxxx.crt file here -----END CERTIFICATE----- </cert> <key> -----BEGIN RSA PRIVATE KEY----- ... <--insert the key body from the xxxx.key file here -----END RSA PRIVATE KEY----- </key>
The privateinternetaccess.com provider has files
ca.rsa.2048.crtandcrl.rsa.2048.pemin its configuration, the contents of which should be inserted between the sections<crl-verify> </crl-verify>and<ca> </ca>respectively.The OpenVPN configuration file will look like this:
client dev tun proto udp remote sweden.privateinternetaccess.com 1198 resolv-retry infinite nobind persist-key persist-tun cipher aes-128-cbc auth sha1 tls-client remote-cert-tls server <auth-user-pass> xxxxxx <--insert your login here xxxxxx <--insert your password here </auth-user-pass> comp-lzo verb 1 reneg-sec 0 disable-occ <crl-verify> -----BEGIN X509 CRL----- ... <--insert the key body from the crl.rsa.2048.pem file here -----END X509 CRL----- </crl-verify> <ca> -----BEGIN CERTIFICATE----- ... <--insert the body of the certificate from the file ca.rsa.2048.crt here -----END CERTIFICATE----- </ca>
Typical errors and solutions:
auth-user-pass without inline credentials data is not supportedThe configuration file contains a line for online login/password entry, which Keenetic does not support. Error in the Keenetic log file:
OpenVPN0 auth-user-pass without inline credentials data is not supported OpenVPN0 Exiting due to fatal error
Delete or comment out all lines of this kind:
auth-user-passBlock-outside-dnsoption errorThe
block-outside-dnsoption is configured on the OpenVPN server, which is correctly handled only in Windows. Error in the Keenetic log file:OpenVPN0 Unrecognized option or missing or extra parameter(s) in configuration: (line X): block-outside-dns (2.4.4) OpenVPN0 Exiting due to fatal error
Add a line to the OpenVPN client configuration file:
pull-filter ignore "block-outside-dns"Error when connecting to PrivateTunnel servers
An error is displayed when trying to connect:
OpenVPN0 Unrecognized option or missing or extra parameter(s) in configuration: (line 3): client-ip (2.4.4)
Add a line to the OpenVPN client configuration file:
ignore-unknown-option client-ip block-ipv6An error occurs when using the askpass
/storage/key.txtoption:Error: private key password verification failed
This is a limitation of the current OpenVPN implementation in Keenetic. You can only use a key without a password or with a fixed password: '
password'.After updating the router to KeeneticOS
3.9.1, the VPN tunnel to the OpenVPN servers for certain VPN suppliers may no longer be established. You can see the following messages in the system log:W [Dec 15 16:52:58] OpenVPN6: DEPRECATED OPTION: --cipher set to 'AES-128-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305). OpenVPN ignores --cipher for cipher negotiations. Error: private key password verification failed
The problem is the outdated encryption format BF-CBC, which is not supported starting from the OpenVPN
2.5.0client version ( KeeneticOS3.9uses the OpenVPN2.6.0client version).Примітка
The
BF-CBCchipher is no longer supported in the default configuration. The OpenVPN2.5.0version supportsAES-256-GCMandAES-128-GCMciphers by default. You can change this behaviour using thedata-ciphersoption, for example, by specifying in the settingsdata-ciphers AES-256-GCM:AES-128-GCM:BF-CBC. To support very old OpenVPN nodes that do not support cipher negotiation (mode "--cipher"), you can specifydata-ciphers-fallback BF-CBC.When upgrading to a new version of OpenVPN, the setting "
cipher BF-CBC" in older configuration files will be converted with appendingBF-CBCto thedata-ciphersset. In addition, thedata-ciphers-fallbackmode is turned on.To successfully install the tunnel, you will need to change the directive:
cipher AES-128-CBCtodata-ciphers AES-128-CBCordata-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305If it doesn't work, then change the directive:
cipher AES-128-CBCtodata-ciphers-fallback AES-128-CBCFor maximum cipher negotiation compatibility with the remote server, specify the following directives:
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305data-ciphers-fallback AES-128-CBCor
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305data-ciphers-fallback AES-256-CBCВажливо
Encryption depends on the remote OpenVPN server. Before changing the directive
cipher, please look at the system log.If the following key size error is recorded in the log:
[E] Dec 16 19:01:38 OpenVPN0: Unrecognized option or missing or extra parameter(s) in configuration: (line 22): keysize (2.6_git) [E] Dec 16 19:01:38 OpenVPN0: Exiting due to fatal error [E] Dec 16 19:01:38 ndm: Service: "OpenVPN0": unexpectedly stopped.Error: private key password verification failed
Then in the tunnel configuration, you need to remove the
keysize 256option directive, which is outdated for the updated client OpenVPN2.6.0, and check the tunnel connection again.You can find detailed information for the "
keysize" option by this link.
We recommend that you read the following information: