Firewall rule examples
To protect your local network from attacks and intruders from the Internet, Keenetic routers have a firewall enabled by default. In most cases, the default settings are sufficient for security, and there is no need to configure the firewall further. But if it is necessary for solving certain issues, any Keenetic router provides flexible options for configuring firewall rules.
In this article, we will give practical examples of firewall rules usage in Keenetic.
Some theoretical information and detailed descriptions of the firewall in Keenetic routers can be found in the article 'How does a firewall work?'.
Важливо
The firewall will not control an existing session when a session is already installed, and then a firewall rule concerning traffic in that session is created. The rule will take effect after the current session is broken — forced or after the session's lifetime has expired.
For the correct operation of the newly created rule (to reset current/active connections), you may disable and enable the corresponding network interface again on your Keenetic.
Let's take a look at the following examples:
Allow Internet access for only one computer in the local network and block access for all others.
Block Internet access for only one computer in the local network.
Allow a particular LAN computer to access only one specified website.
Allow Internet access from the local network only by specified protocols (services).
Block certain hosts on your LAN from accessing the router's web interface
We will configure firewall rules via the Keenetic web interface. You can do this on the Firewall page.
Примітка
To block Internet access, we will define the TCP protocol in firewall rules because the Internet is based on the TCP/IP network data transfer protocols.
Allow Internet access for only one computer in the local network and block access for all others.
In this example, you need to create two rules for the 'Home segment' interface.
First, we will create a Permit rule where you define the source IP address (the computer's IP address to be allowed to access) and the TCP protocol type.
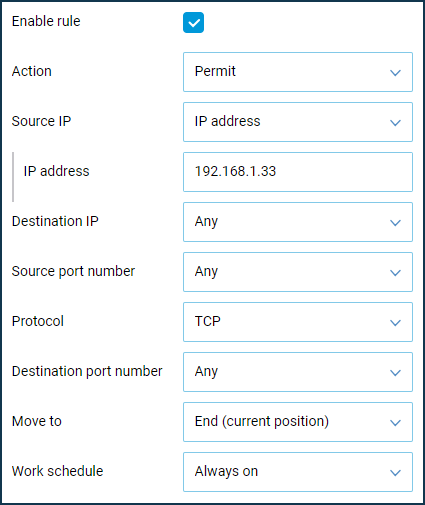
Then we will create a Deny rule where we define the source IP address as a subnet (
192.168.1.0with a mask of255.255.255.0) and the TCP protocol type.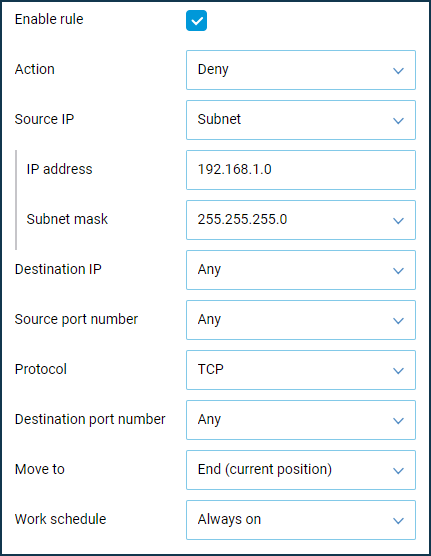
Важливо
This rule should be configured from a computer that can access the Internet. Otherwise, you will lose access to the Keenetic web interface after creating the rules mentioned above. If this happens, manually assign the permitted IP address in the network adapter settings and connect to the web interface.
Block Internet access for only one computer in the local network.
In this example, we need to create one rule for 'Home segment'. We will create a Deny rule where we set the source IP address (the computer's IP address which access will be denied) and the TCP protocol type.
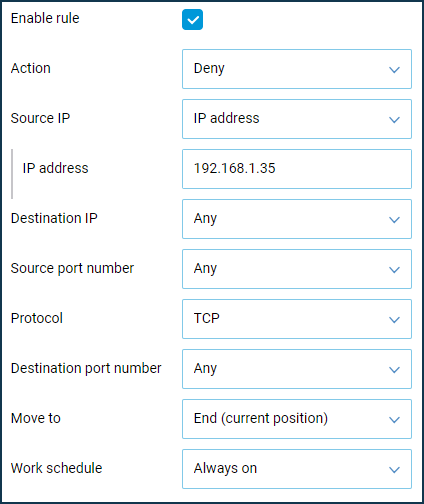
Block access to a particular website from a local network.
This example will block all computers in the local network from accessing the Wikipedia website wikipedia.org.
Важливо
Domain names cannot be used in the firewall settings of Keenetic routers, and only IP addresses can be set.
Before configuring the rules, you need to find out the IP address of the website you want to use. One site may have several different IP addresses (it usually refers to large resources such as amazon.com, google.com, facebook.com, etc.).
The first way to find out the website's IP address is to use a special command '
nslookup <web site name>'.For example, in the command line of the operating system, we will run the command:
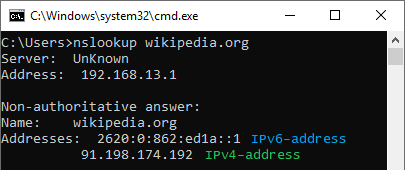
The result of the command above will allow you to see the IP addresses where the website is located (in our example, wikipedia.org uses only one IP address,
91.198.174.192).The second way to find out the website's IP address is to use one of the special online services (for example, 2ip.io). In a special field, you will need to specify the name of the website you are interested in and press the 'Check' button. After that, you will see all IP addresses on which the website works.
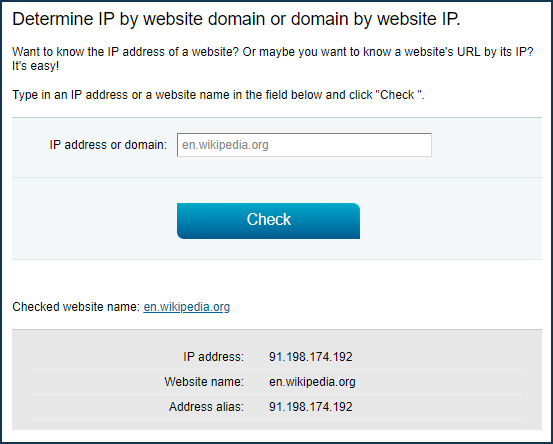
Now that you have the IP address of the website, you can begin creating firewall rules.
Важливо
Websites can run not only on HTTP but also on HTTPS.
Since the website uses a single IP address in this example, let's create two rules for 'Home segment' to block traffic by protocols: one for HTTP and one for HTTPS. Create Deny rules to specify the destination IP address (the IP address of the site to be denied access to) and the protocol type (HTTP and HTTPS).
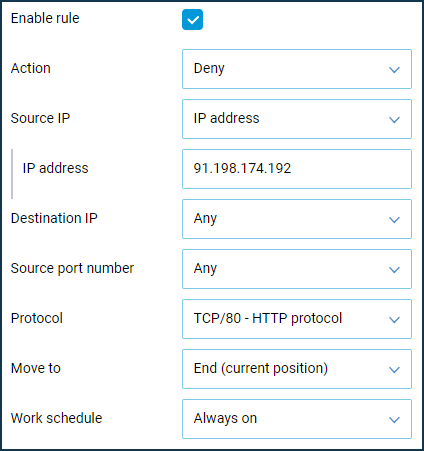
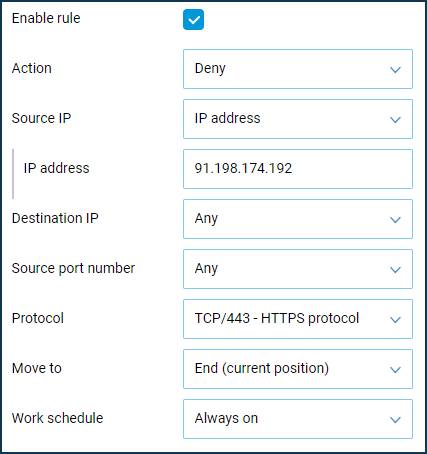
More information can be found in the article How to block access to a specific site.
Allow a particular local computer to access only one specified website.
In this example, let's allow a local computer with an IP address of 192.168.0.31 to access only the Wikipedia.org website.
Access to other Internet sites will be blocked for this computer.
First, let's find the IP address of the website we need. In our example, this is
wikipedia.org, and its IP address is91.198.174.192. Detailed information on finding the website's IP address can be found in Example 3 of this manual.In this example, you need to create three rules for the 'Home segment'. First, we will create a Permit rule that defines the source IP address (the IP address of the computer that you want to allow access to), the destination IP address (the IP address of the website that you want to allow access to), and the HTTP and HTTPS protocol types.
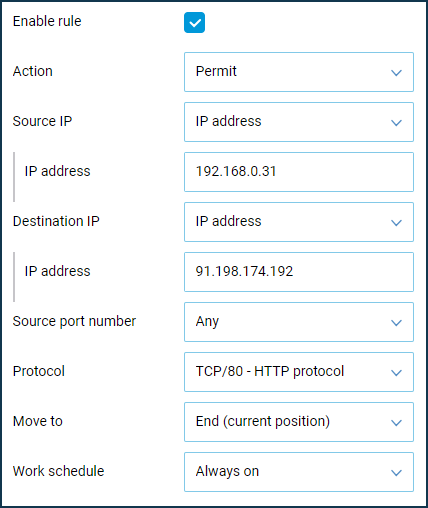
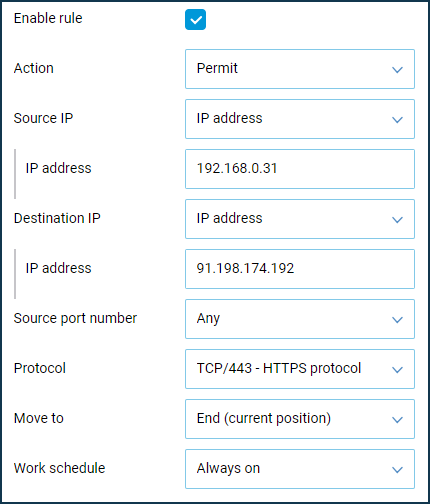
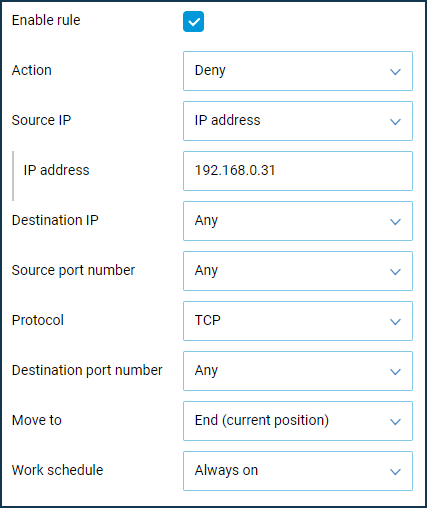
Then we will create a Deny rule where we specify the source IP address (the computer's IP address to be denied access to) and the TCP protocol type (to block the Internet access).
Allow Internet access from the local network only by specified protocols (services).
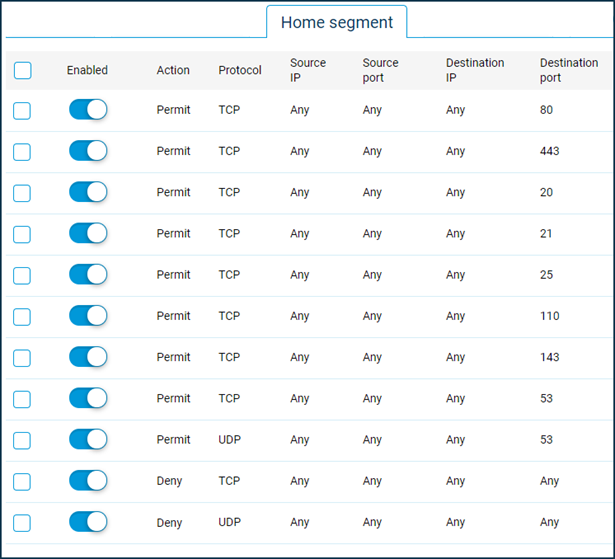
Let's allow local computers to access the Internet only via HTTP, HTTPS, FTP, SMTP, POP3, IMAP, DNS and block all other traffic.
In this example, you need to create rules for 'Home segment'. First of all, we will create Allow rules where we specify the value 'Any' in the fields 'Source IP' and 'Destination IP', and in the 'Protocol' field, we select the necessary type of protocol (service) from the list. Then we create two Deny rules, where we set the value 'Any' in the fields 'Source IP' and 'Destination IP', and in the 'Protocol' field, the value of TCP and UDP to block Internet access.
Важливо
For the correct Internet functioning, it is necessary to have the Domain Name Service (
TCP/53,UDP/53), which allows converting symbolic names of sites/domains into IP addresses (and vice versa).In our example, we have the following set of firewall rules:
Allow remote control of the Keenetic router.
Важливо
Access to a Keenetic router (its web interface) from an external network (the Internet) is blocked by default. This is implemented for the device and local network security.
Access to the device from the Internet is possible if there is a public IP address on the external interface (WAN), through which the router connects to the global network. To access a router with a private IP address, you should use the KeenDNS service.
In this example, we will create a firewall rule to provide remote control of the router from the Internet (particularly to connect to the device's web interface).
We will also allow ICMP ping requests from the Internet (this will allow you to check the availability of the device on the network).
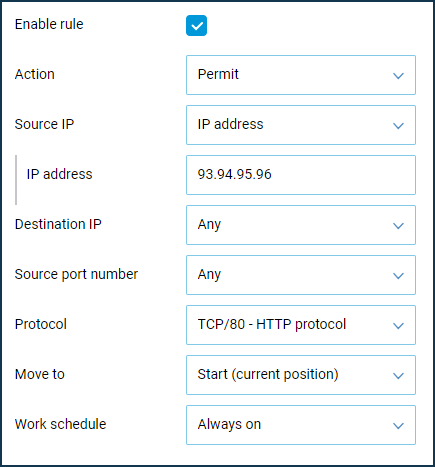
To increase security, we will allow remote control and ping from the external network from a defined public IP address only (in our example, from the IP address
93.94.95.96).Важливо
If you use a public IP address, we do not recommend allowing access to the Keenetic web interface and allowing ping requests for all users from the public (global) network.
In this example, we need to create rules for the 'Provider' external network interface. This means the interface through which you access the Internet (it can be PPPoE, PPTP, USB LTE, Yota, etc.).
We will create a Permit rule where we fill the 'Source IP' field (the public IP address of the computer to which access from the Internet will be allowed), and in the 'Protocol' field, select 'TCP/80 (HTTP)'.
Then we will create a similar rule but for the ICMP protocol (for ping utility).
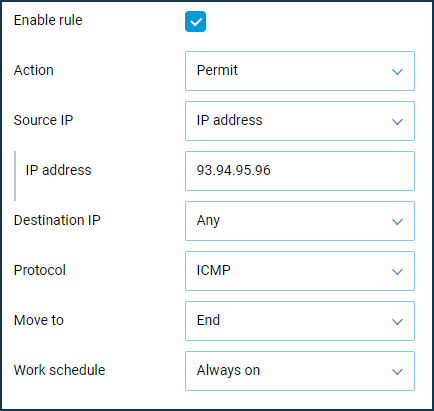
Thus, pinging the Keenetic router (via ICMP) and accessing its web interface (via HTTP) will be possible from the Internet, only from a certain IP address.
Важливо
In a web browser, you need to use the public WAN IP address of the Keenetic in the global network to access its web interface (you can see it in the Keenetic's web interface on the 'System dashboard' start page on the 'Internet' information panel by clicking 'More details' in the 'IP address' line). The address in the browser should start with
http://, i.e.http://IPaddress (e.g. http://89.88.87.86).Block access to Keenetic from the IP addresses of a defined Internet subnet or an external network.
Imagine that you have detected frequent attempts to access (an attack) the router's WAN port from unknown IP addresses from the Internet. For example, connection attempts come from different IP addresses, but they all belong to the same
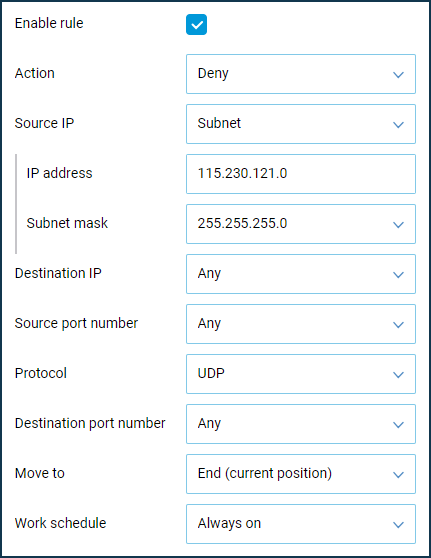
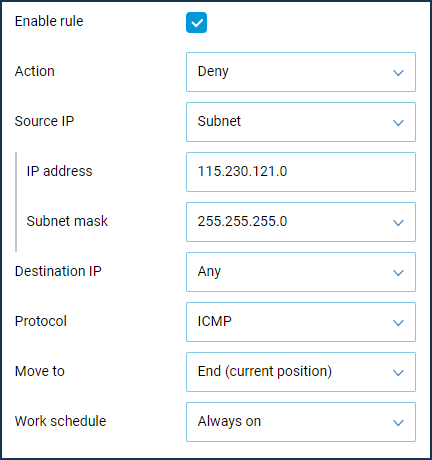
115.230.121.xsubnet.In this case, on the Keenetic external interface 'Provider' (or another one through which the Internet is accessed), it is necessary to block access to the WAN port for IP addresses of the subnet
115.230.121.x.Let's create the Deny rules for TCP/UDP/ICMP(ping) traffic, where we should set the 'Subnet' value as 'Source IP' and specify the subnet address and mask. When using a subnet mask with the prefix
/24 (255.255.255.0), the subnet's IP address should end with0(in this example, it is115.230.121.0).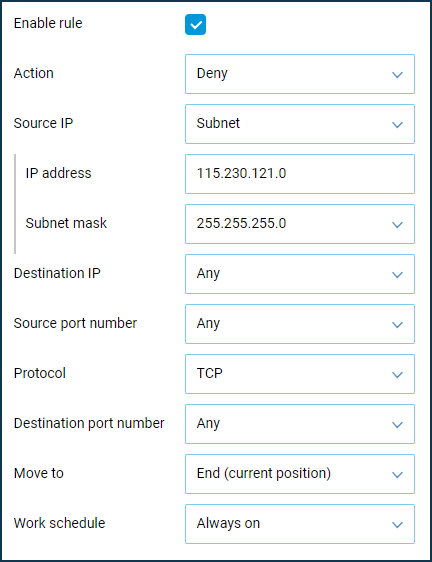
Allow RDP access only from a specific external IP address.
Let's suppose that a Keenetic router uses a port forwarding rule to allow connection from the Internet to a home computer via RDP (TCP/3389). However, in this case, the port will be open for any IP address from the Internet. It is recommended that you allow RDP access from a specific external IP address only for security reasons. This can be done using firewall rules on the external interface through which the Internet is accessed.
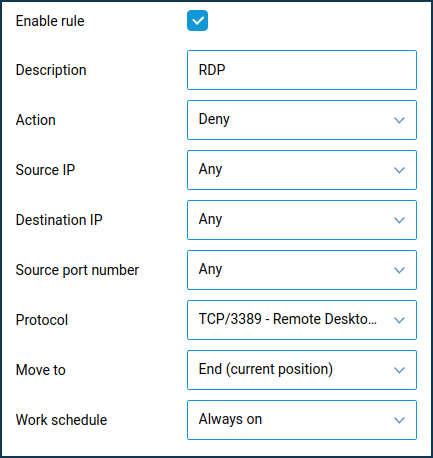
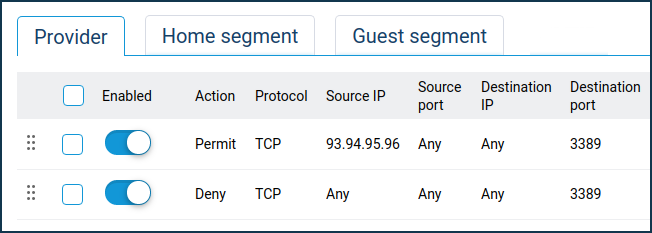
Create a Permit rule for access from a specific IP address on TCP port 3389 and then create a Deny rule for all IP addresses on TCP port 3389.
In our example, only connections from public IP address
93.94.95.96are allowed.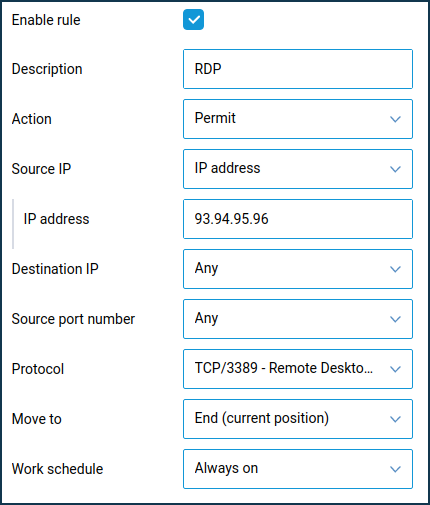
Важливо
If you configured destination port mapping in the forwarding rule (e.g. from
4389to3389), in the firewall rule, you must specify the actual destination port number used on the server in the local network, i.e.3389.Block certain hosts on your LAN from accessing the router's web interface
If you need to block access to the Keenetic web interface at 192.168.1.1 and my.keenetic.net for some devices on your local network, you can do that using firewall Deny rules created on the LAN interface (which is the 'Home segment' interface by default).
Let's see an example of blocking access to the router's web interface for the device with IP address
192.168.1.143.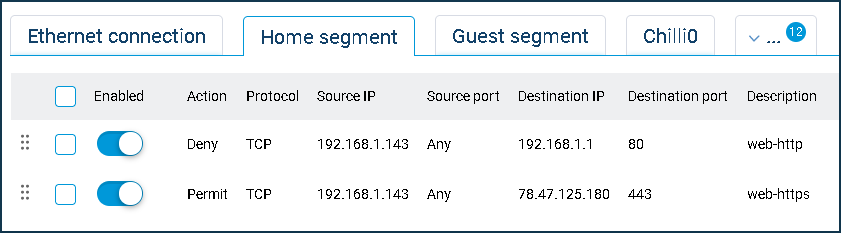
In our example, we have added two Deny rules. The source address is the IP address of the local network host that we want to block access to the router's web interface. Note that in the rule to deny access to
192.168.1.1, the destination port should be set to TCP/80, and in the rule to Deny access to my.keenetic.net, the destination address should be78.47.125.180(which is the IP bound to the domain name my.keenetic.net) and port TCP/443 (because access to the domain name is automatically redirected to the HTTPS protocol).We have shown an example to block one host from accessing the router's web interface from the local network, but similarly, rules can be made for other hosts.
Примітка
Question: Is it possible to block traffic between only two hosts in a local network using Firewall rules?
Answer: Firewall cannot block traffic between two hosts on the same LAN because the hosts are in the same segment, and the communication between them takes place at the second layer of the OSI model. The firewall works at
layer 3of the OSI model.Traffic can only be blocked between hosts in different network segments - by enabling the '
isolate-private' function (blocks all communication between segments) or using separate Firewall rules, blocking access only for some hosts.