KeeneticOS 4.2
KeeneticOS release notes for Keenetic Giga (KN-1010) in the Main Channel
KeeneticOS releases in this channel have passed our full rigorous testing and are recommended to all users, to avoid issues and maximize capabilities. This channel is updated roughly every two-three weeks with minor releases, and every two months with major releases.
Keenetic Giga (KN-1010) is currently in the Standard Updates support period and receives regular software updates, including security enhancements, new features, operating system updates, and bug fixes.
What’s new?
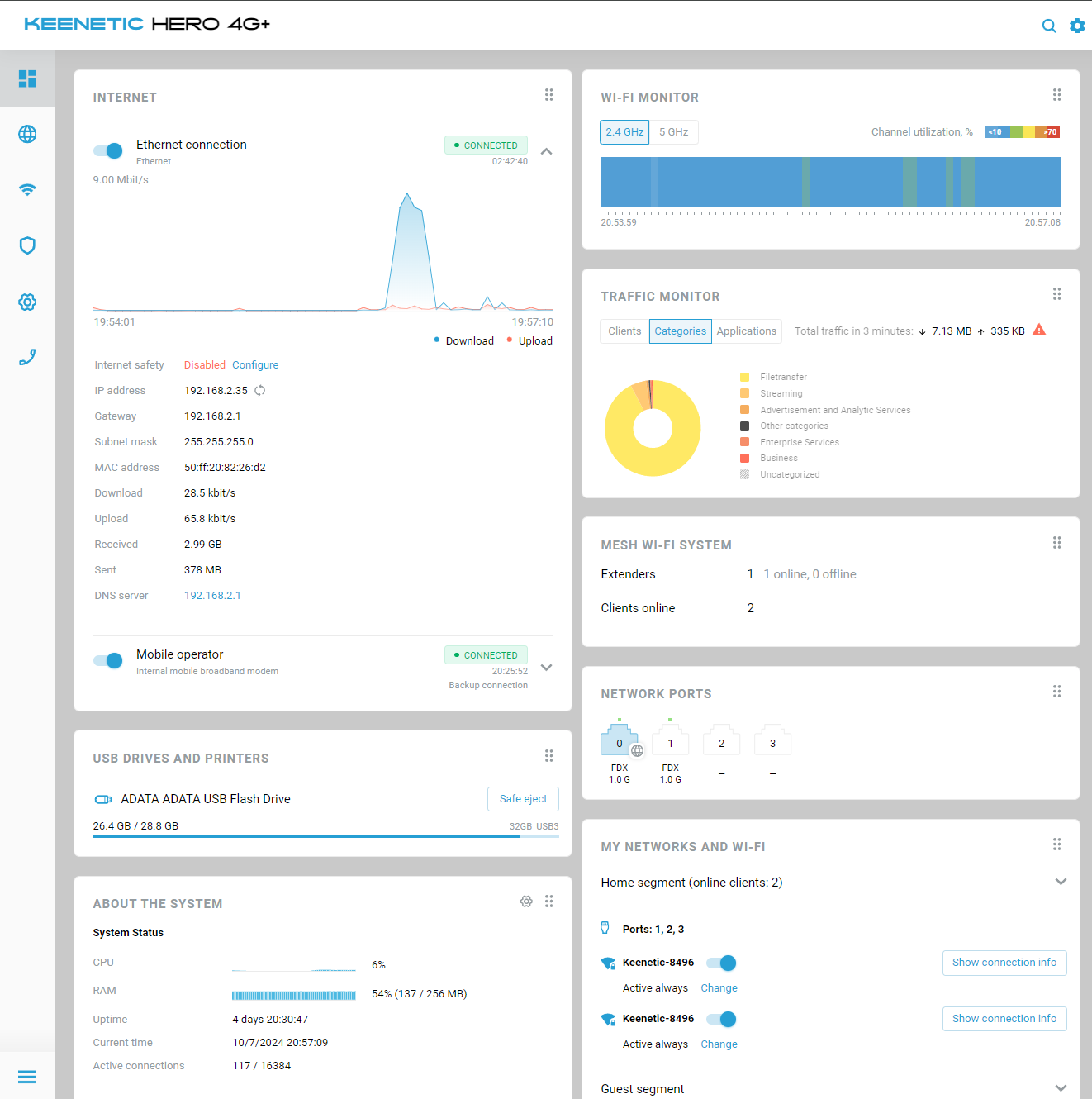
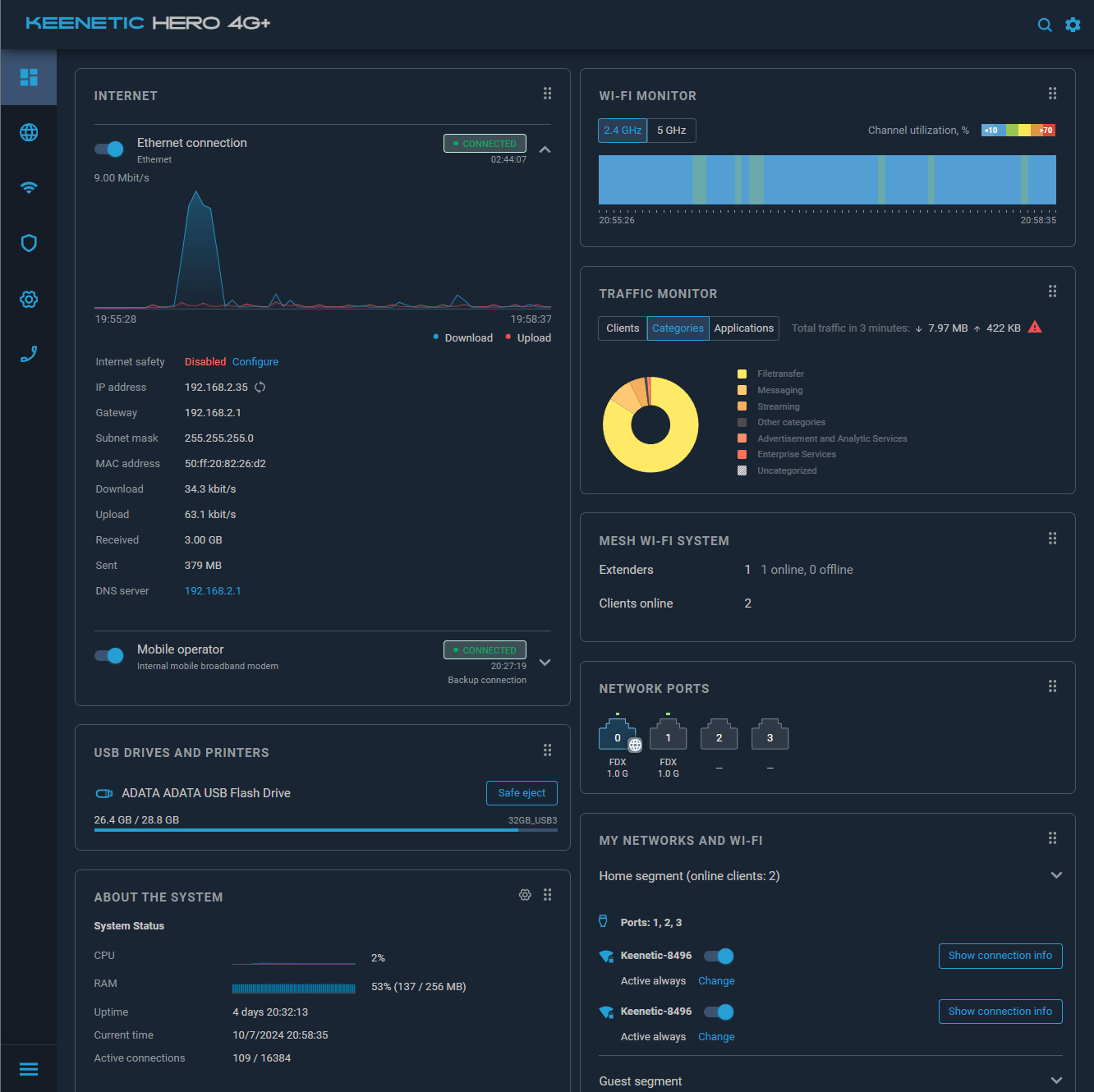
Welcome to KeeneticOS version 4.2! As usual, we have several performance improvements and bug fixes, but our main focus for this update is to introduce the new Web Interface and further improve support for the IPv6 protocol in various KeeneticOS services.
The new Web Interface has a refreshed look, with light and dark themes to choose from, and carefully selected usability enhancements. We've moved to an updated framework that supports modern security enhancements.
It is now possible to update KeeneticOS on all devices in the Wi-Fi system with a single click. In addition, the Autoupdate function automatically manages the updates of the connected extenders according to the schedule of the main router.
Clients connecting to the Home segment of the network are now automatically registered by default, improving security and ease of management.
The new Segment Default Policy option improves Internet access management for network clients. By default, a registered client will follow the connection policy associated with the network segment it is connecting to. For example, you can set up a separate Wi-Fi network at home with the same name as your office network and route its traffic to a VPN connection to your office. Then, when working from home, simply switch to the office Wi-Fi network to teleport immediately.
The new OpenConnect VPN server and client are now available. Connect networks or access your network remotely using free applications available for Android or iOS.
KeeneticOS 4.2.4
18/12/2024
Fixed
The following fixes have been applied to the Web interface.
Fixed selection of networks with WPA3 protection from the list of available networks on the Wireless ISP page. [NWI-3937]
Fixed the incorrect Applications not installed status on the System Dashboard page. [NWI-3798]
Fixed tooltips display on the Traffic Monitor page in the Web interface. [NWI-3894]
Fixed the display of certain usernames in the User Accounts configuration popup. [NWI-3898]
Fixed the sorting of the Uptime column in the Mesh Wi-Fi System nodes table. [NWI-3815]
Fixed the flickering when loading the Home segment page. [NWI-3820]
Fixed menu section headings. [NWI-3824]
Fixed tooltips on the Traffic Monitor page in mobile view. [NWI-3825]
Fixed the auto-completion on the
/webclicommand line interface page. [NWI-3791]Fixed the display of long strings in the built-in search results. [NWI-3866]
Fixed an incorrect operation timeout in the DNS proxy service when waiting for the upstream DNS server to respond under certain conditions. [SYS-1245]
Fixed a bug where WireGuard VPN would attempt to reconnect after the underlying interface was shut down. [NDM-3560]
The VPN Server's clients (PPTP, SSTP and OpenConnect) will now access the Internet according to the connection policy of the local network to which the server is connected. [NDM-3563]
Fixed an issue with incorrect WireGuard VPN uptime under certain conditions. [NDM-3567]
KeeneticOS 4.2.3
20/11/2024
New
The option to select the OS update channel for Wi-Fi System Extenders is now available in the Wi-Fi System Controller Web interface. [NWI-3823]
The new options have been implemented in the Web interface.
The Cards Position popup receives the Reset button to restore the original order. [NWI-3702]
All Wi-Fi access points in the segments are now displayed on the System Dashboard page's card. [NWI-3743]
Improved
The improvements have been applied to the Web interface.
Improved the Active Connections table. [NWI-3703]
Changed colours on the Traffic monitor charts for better visibility and contrast. [NWI-3699]
The maximum Username length for Proxy connections increased to 128 characters. [NDM-3512]
The DDNS service now re-attempts to update the Domain name resolution 30 seconds after a failed attempt. [NDM-3513]
Enabled LLDP multicast in addition to broadcast announcements to improve compatibility with managed Ethernet switches. [SYS-1214]
Fixed
Fixed an issue where the SFTP connection to the SFTP Server would hang after transferring 476 megabytes. [SYS-1240]
Fixed a KeenDNS issue with Internet access to web applications with the No access (
security-level private) setting enabled. [NDM-3479]Fixed an issue with setting
speed automode for SFP/MDI combo port. [NDM-3537]Fixed an issue with the OpenConnect VPN client reconnecting when the remote OpenConnect VPN server is restarted. [NDM-3532]
The following fixes have been applied to the Web interface.
Fixed problem where System Dashboard cards were not editable on mobile screens. [NWI-3865]
Removed domain-specific DNS entries from the Signal levels dialog. [NWI-3784]
Fixed an issue with downloading of packet capture files when using a USB drive as a storage location. [NWI-3790]
Optimized the internal logic of the System log popup window. [NWI-3813]
Fixed tooltip display for Static IP fields. [NWI-3818]
Fixed the view mode selector behaviour on the Applications page. [NWI-3827]
Fixed JS errors on the General System Settings page. [NWI-3840]
Fixed the display of the Media library folder path for the Media server application. [NWI-3852]
The following fixes have been applied to the Web interface.
Fixed the position of the Other management options link on mobile devices. [NWI-3722]
Fixed an issue where the USB disk would disappear from the USB Devices section when unmounting all partitions. [NWI-3762]
Fixed tooltips for Wi-Fi toggles on Extenders in the Mesh Wi-Fi system. [NWI-3763]
Fixed the scrollbar colour for the Dark theme. [NWI-3764]
Fixed the scrolling on mobile devices. [NWI-3768]
Fixed Applications availability conditions. [NWI-3770]
Fixed JS errors when a segment's configuration page is open. [NWI-3779]
Fixed line wrapping when menu is expanded. [NWI-3780]
The placement of the Bandwidth control header on the Connection Policies page has been corrected. [NWI-3781]
Fixed the colour of the operating mode radio buttons. [NWI-3714]
Fixed the Wi-Fi Channel number configuration and notifications when using Wireless ISP (WISP). [NWI-3698]
Fixed the USB modem status display. [NWI-3707]
Fixed the DHCP Address pool size calculation. [NWI-3720]
Fixed the highlighting in the Ports and VLANs Settings section when editing settings. [NWI-3789]
Fixed removal of the DNS server for the WireGuard VPN connection. [NWI-3800]
Fixed incorrect display of 802.1x Authentication settings without component installed. [NWI-3822]
Fixed communication with remote NTP time server via IP alias. [NDM-3417]
An issue that caused the
sent too big header while reading response header from upstreamerror message to appear in the System log when accessing the web applications via KeenDNS. [NDM-3480]Resolved a software packet engine (
ppe software) incompatibility with incoming traffic having TTL 1. [NDM-3490]Fixed removing the DNS (
ip name-server) record with the default port. [NDM-3493]Fixed listing of Ethernet connections. [NDM-3504]
Fixed an issue that caused the
Bridge: wrong port indexerror message to appear in the System log when displaying the Client lists page. [NDM-3514]Fixed saving of Server address field with "camouflage" suffix in SSTP VPN client settings. [NDM-3521]
An issue that caused the
https-dns-proxy: curl needed more event than max connectionserror message to appear in the System log has been fixed. [NDM-3523]
KeeneticOS 4.2.1
11/10/2024
New
The Wi-Fi System Controller is now able to manage the KeeneticOS update channel on the Wi-Fi System Extenders. [NDM-3419]
mws member {member} update channel {channel}— set KeeneticOS{channel}on an extender{member}
New USB modems are now supported, including:
ZTE MF79N 4G LTE Cat4 USB modem. [NDM-3451]
Vodafone K4606 3G USB modem. [NDM-3483]
Added descriptions of LTE modem signal metrics to the Show signal levels popup. [NWI-3750]
The new public DNS resolver presets from ControlD are now accessible on the Internet Safety page. [NDM-3452]
The
opkg diskcommand line interface (CLI) has been augmented with a new URL option, which enables downloading of the remote OPKG installation archive. [NDM-3453]opkg disk ({disk} | {disk}) [{url}]— set{url}of the remote OPKG archive.For example:
opkg disk storage:/ https://bin.entware.net/aarch64-k3.10/installer/aarch64-installer.tar.gz
A standalone
Policy Tablemode has been implemented, which disables the automatic addition of static routes to the selected connection policy. [NDM-3445]ip policy {name} standalone— enablestandalonemode for connection policy{name}.
WireGuard client connections now select a random listen port each time the tunnel reconnects. [NDM-3469]
Added a CLI command to unbind the DDNS service requests from the specified interface. [NDM-3420]
interface {name} dyndns nobind— disable DynDNS bind on interface{name}.
Implemented a CLI command to enable the sending of the
client IDfor the WireGuard connection peer. [NDM-3427]interface {name} wireguard peer {peer} client-id send {value}— setclient-idas a decimal{value}of the required hexadecimal ID for Wireguard{peer}.
Added a CLI command to configure the
authgroupvalue for the OpenConnect connection to ensure third-party compatibility. [NDM-3430]interface {name} openconnect authgroup {authgroup}— set the{authgroup}value to use with OpenConnect interface{name}connection.
When accessing the Internet over the tunnel, clients of IKEv1/IPsec and IKEv2/IPsec VPN Server applications now follow the connection policy selected for the bound network segment. [NDM-3431]
We are introducing the next-generation Web interface as the standard UI for configuring and managing your Keenetic device. [NDM-3378]
You can now assign Network ports on Extender devices to any configured network segment using the Command Line Interface (CLI). Alternatively, you may wish to disable the Network ports for security reasons. [NDM-3162]
mws member {member} port {port} [no] access {interface}— assign{port}on a{member}node to access an{interface}segment;mws member {member} port {port} [no] disable— disable{port}on a{member}node.
Enhanced software packet processing engine to enable acceleration for traffic with a manually set TTL value. [SYS-1157]
The new IntelliQoS option allows 802.1p priority code point (PCP) mapping for egress packets in the command line interface (CLI). [NDM-3318]
interface {name} vlan qos egress map {priority} {pcp}{priority}— NTCE priority queue number. Use0to assign the same PCP value to any outgoing packet on the interface;{pcp}— set the new value of the 802.1p priority code point.
The implementation of a ZeroTier connection now includes accepting managed routes and DNS servers published on the ZeroTier network controller. [NDM-3319]
The
camouflagemode option has been added to both SSTP VPN and OpenConnect VPN servers and clients, providing greater security against remote service scanning. [NDM-3257]oc-server camouflage— enablecamouflageoption for the OpenConnect VPN serversstp-server camouflage— enablecamouflageoption for the SSTP VPN server
The new OpenConnect VPN client system component is now available, allowing you to establish a secure connection to a remote server via the command line interface (CLI). [NDM-3207]
A new CLI
grepextension is now available to filter the output of theshowcommand. [NDM-3075]grep [-A <n>] [-B <n>] [-C <n>] regex— trim theshowcommand output using theregexregular expression.-A— number of XML nodes to show after match.-B— number of XML nodes to show before match.-C— displayed XML cluster depth.
For example:
(config)>
show interface | grep addressInterface, name = "Home" address: 192.168.2.1 ipv6: Interface, name = "Guest" address: 10.1.30.1 ipv6: (config)>show system | grep cpuloadcpuload: 5
A new segment default policy for hosts has been implemented and is now enabled by default. Registered devices with this connection policy assigned will follow the default connection policy of the network segment they are connecting to. [NDM-2237]
ip hotspot host {MAC} conform— set host with specified{MAC}to follow the current segment's connection policy.
The new application filtering option is now available in the Application traffic analyser service via command line interface (CLI). This option allows to create a filtering profile, add required applications, assign a host or segment to the filtering profile and enable the operation schedule. [NDM-3069]
ntce filter profile {name} application {application}— add an application to the profile.ntce filter profile {name} group {group}— add an application group to the profile.ntce filter profile {name} type {type}— set the profile type, which can bepermitordeny.ntce filter profile {name} description {description}— set the profile description.ntce filter profile {name} schedule {schedule}— set the profile schedule.ntce filter assign host {host} {profile}— assign a profile to a registered host (MAC address).ntce filter assign interface {interface} {profile}— assign a profile to an interface.
The new option to automatically register hosts in the Home segment is now available (enabled by default). You can disable this behaviour using the command line interface (CLI). [NDM-3101]
ip hotspot auto-register disable— disable automatic host registration for the Home segment.
The new OpenConnect VPN server system component is now available, providing a remote SSL VPN connection to your Keenetic. [NDM-3141]
oc-server interface {interface}— bind OpenConnect server to an interface.oc-server pool-range {begin} {size}— set OpenConnect address pool.oc-server static-ip {name} {address}— set static IP address for a user.oc-server mtu {mtu}— set OpenConnect server MTU.oc-server multi-login— enable multiple connections with the same user account.ip nat oc— enable NAT for OpenConnect clients.service oc-server— enable OpenConnect service.
The Keenetic Phone Station system component now supports the filtering of incoming calls. [VOX-271]
nvox sip {id} whitelist {digitmap}— create whitelist for SIP{id}with specified{digitmap};for example:
nvox sip 1 whitelist +1111x.|+2222x.|2389x.|32756— allows phone calls with numbers starting from+1111,+2222,2389and an32756number.nvox sip {id} blacklist {digitmap}— create blacklist for SIP{id}with specified{digitmap};for example:
nvox sip 1 blacklist +3333x.— block phone number starting from+3333.nvox sip {id} enable-whitelist— enable whitelist for SIP{id}.nvox sip {id} enable-blacklist— enable blacklist for SIP{id}.show nvox sip {id} whitelist— display allowlist settings.show nvox sip {id} blacklist— display blocklist settings.
The Keenetic Phone Station system now supports import of the phonebook from a file. [VOX-326]
nvox phonebook import {filename} {mode}— import contacts in the vCard format.filename— *.vcf filename;mode— import mode:replace,overwrite,extend, orduplicate.
nvox phonebook delete— delete all contacts from the phonebook.nvox sip {id} enable-whitelist-phonebook— enable phonebook as an allowlist filter for incoming calls.show nvox phonebook— display all phonebook records.
Improved
Mesh Wi-Fi system controller now propagates segments without Wi-Fi access points to extenders. [NDM-3210]
Disabled DTLS (Datagram Transport Layer Security) support for the OpenConnect VPN server in KeenDNS cloud mode to improve compatibility with the VPN Client Pro application. [NDM-3394]
Enabled caching of the saved configuration to improve the Web interface response time and reduce CPU load. [NWI-3643]
Implemented dynamic table size adjustment with
nf_conntrack_maxvalue forsoftware ppe(Packet Processing Engine) when the user changes maximum NAT sessions via command line interface (CLI). [NDM-3344]
The SNTP service compatibility enhancement adds support for
Reference IdentifierandReference Timestampvalues in SNTP responses based on RFC4330. [NDM-3368]
The OpenSSL library has been moved to a different branch with the latest version
3.0.13. [SYS-1152]Improved robustness of the DNS over TLS and DNS over HTTPS server cache. [NDM-3320]
The clients of the VPN Server (PPTP, SSTP and OpenConnect) now access the Internet following the Connection Policy of the local network to which the server is bound. [NDM-3295]
The implementation of IKEv1/IKEv2 IPsec VPN servers now allows to avoid IP address conflicts with other interfaces. [NDM-3250]
Improved host detection using
EchoReqin theICMPv6protocol to ensure correct operation of port forwarding rules for the IPv6 protocol. [NDM-3265]Optimized the memory consumption of the SMB file and printer sharing system component when using the Cx File Explorer mobile application. [NDM-2927]
Added SMS subsystem support for Fibocom FM350 and Quectel RM500U modem modules. [NDM-3267]
The Phase 2 of the site-to-site IPsec tunnel now supports the SHA512 HMAC algorithm. [NDM-3269]
crypto ipsec transform-set {name} hmac esp-sha512-hmac— enableesp-sha512-hmacalgorithm for transform-set{name}
Added MAC address and registration time information to the name of devices registered automatically. This will help you easily identify and keep track of the devices on your network. [NDM-3253]
DNS over HTTPS (DoH) now supports secure name resolution over the HTTP/3 protocol. [NDM-3229]
Implemented an
aggressivemode option for the IKEv1 client in the command line interface (CLI) for compatibility with VPN (IPsec) servers running on Fritz!Box routers. [NDM-3227]interface {name} ipsec aggressive— set theaggressivePhase 1 mode for VPN connection{name}
A new read/send timeout option allows the session lifetime for Web applications of the KeenDNS proxy service to be set via the command line interface (CLI). [NDM-3157]
ip http proxy {name} timeout {timeout}— set{timeout}for KeenDNS{name}proxy.
The WireGuard advanced security configuration (ASC) parameters are now available in the command line interface (CLI). [NDM-3202]
interface {name} wireguard asc {jc} {jmin} {jmax} {s1} {s2} {h1} {h2} {h3} {h4}— set additional ASC parameters for WireGuard{name}tunnel.
Disabling Port Forwarding (
ip static) rules now forces matching active sessions to be dropped. [NDM-3067]Implemented new options to preserve Referer and Origin headers for Web applications of the KeenDNS proxy service in the command line interface (CLI). [NDM-3089]
ip http proxy {name} preserve-referer— preserve Referer header for{name}of the web proxy rule.ip http proxy {name} preserve-origin— preserve Origin header for{name}of the web proxy rule.
A NetFlow monitor system component can now collect IPv6 traffic information and monitor network flows. [NDM-3109]
The
MOBIKEextension (RFC 4555) has been enabled for both the IKEv2/IPsec VPN Server and the IKEv2 client. [NDM-3164]
Fixed
Fixed issue with saving of Wireguard®
connect viasetting. [NDM-3467]Fixed a problem that caused an
unable resolve NAT64 domainerror message on a CLAT interface. [NDM-3484]Fixed an issue where the Mesh Wi-Fi System would not work correctly with extenders using KeeneticOS version
3.7. [NDM-3491]Fixed an issue with the
communityfiltering for SNMPv1 protocol. [SYS-1203]
Restored the correct work of access to my.keenetic.net restriction from local network segments configured to prohibit services hosted on the Keenetic device. [NDM-3346]
Fixed the display of the Mesh Wi-Fi System clients shifting between bands in the Transition Log. [NDM-3412]
Fixed the socket leak in
nf_queue. [NDM-3428]
Fixed an issue where IPv6 static DNS configuration entries were cleared after the device started. [NDM-3390]
Resolved the issue causing unstable connectivity between local and remote networks in a multi-subnet configuration of a site-to-site IPsec VPN tunnel, secured in Phase 1 by IKEv1. [NDM-3381]
Fixed the display of the Transition Log for Mesh Wi-Fi system clients on mobile devices. [NWI-3579]
Fixed incorrect application of a DNS query filtering rule for IPv6 link-local addresses that occurred under certain conditions. [NDM-3379]
Fixed the PPTP VPN connection stalling on the backup connection after the primary connection is restored. [NDM-3376]
A problem that caused the
OpenVPN: Connection reset, restartingerror message to appear in the System log has been fixed. [NDM-3355]
Fixed IPv6 ULA (Unique local address) prefix announcements with incorrect
Abit. [NDM-3350]The L2TP/IPsec VPN client now uses a random source port to avoid connection problems when multiple VPN L2TP/IPsec connections are established behind NAT on an upstream router. [NDM-3349]
Fixed selection of the best node for wireless backhaul connection in the Mesh Wi-Fi System. [SYS-1161]
Fixed IPv6 traffic accounting with the hardware packet processing engine disabled. [NDM-3234]
Fixed remote access over an IKEv2/IPsec VPN connection to a local network host for which a SNAT mapping rule is configured. [NDM-3310]
Fixed the DynDNS domain name validation; now it's possible to use only one domain. [NDM-3309]
Enabled the SNMP reports by OID
ifAdminStatusto monitor the operational state of device ports via third-party software. [NDM-3296]
Fixed the forwarding of the source IP address in the
X-Real-IPheader when accessing web applications via KeenDNS. [NDM-2214]Fixed access to the KeenDNS Web Applications configured with prohibited remote access (
security-level private) from the home network. [NDM-3264]
Incomplete application of static IPv6 routes when re-establishing an associated VPN connection after a reboot fixed. [NDM-3248]
UPnP service rules are now correctly applied to clients accessing the Internet using the Connection policy with active multipath mode. [NDM-3251]
Fixed DNS query interception in the additional network segments. [NDM-3228]
Fixed priority of user-defined
ip staticrules over automatic UPnP port forwarding rules to a host. [NDM-3078]Fixed home network access for L2TP/IPsec VPN server clients when
ip staticrules are configured on WAN IP aliases. [NDM-3110]Fixed binding to the WAN address and inbound access to the service port for the ZeroTier client connection. [NDM-3216]
Fixed iOS L2TP/IPsec client disconnecting under heavy load. [NDM-3180]
The CloudFlare content filter has been corrected to work properly on networks that do not support IPv6. [NDM-3163]
Fixed port forwarding issues after Hotspot (
ip hostspot) code refactoring. [NDM-3127, NDM-3171]