KeeneticOS 3.4
KeeneticOS 3.4.12
16/7/2020
New
The single-band Wi‑Fi Keenetic models can now acquire dual-band Wi‑Fi extenders to Wi‑Fi system and deploy 2.4 GHz back-haul connections between Wi‑Fi System nodes. [NDMS-819]
Further modem support: The high-speed LTE Cat6 Sierra EM7455 modem is now supported. [NDMS-805]
Improved
In case of Wireless ACL using Blacklist access control mode, newly registered devices will no longer be automatically added to the blacklist. [NDW-1108]
For the purpose of Keenetic firmware image size optimization, the maximum number of installed languages in the system is limited to three. [NDW-1127]
The new firmware signing certificate is deployed to the cloud infrastructure. Previously saved firmware files can be uploaded using the TFTP recovery mode only. [NDMS-828]
Fixed
Initial setup wizard could not start after restoring factory settings on device. [NDW-1198]
KeeneticOS 3.4.6
10/6/2020
New
Further modem support: The 3G modem Huawei E3131 is now supported. [NDMS-775]
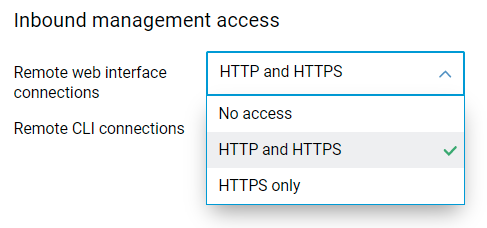
The Inbound management access control setting in the Web Interface of the Wi‑Fi system controller will apply to all Wi‑Fi system extenders. [NDW-1006]
Improved
The colon symbol
:in HTTP Cookie headers is now supported. It allows the support of non-RFC based Web interfaces of network devices which are available via the Port forwarding setting. [NDMS-779]
Fixed
The description of WebDAV server password status has been rewritten if the setting Ignore access control is active. [NDW-1004]
The incorrect empty list of Extenders in Wi‑Fi System is fixed. It occurred if one of Extenders was in offline mode. [NDW-1044]
The evaluation of nesting of bridged interfaces is corrected. Currently, the configuration order of
interface bridge[x]interfaces is processed rightly. [NDMS-765]The QMI interface for 4G/3G USB modems system component now works properly with certain operator branded Huawei E392 modems. [NDMS-758]
An error in the Wi‑Fi Protected Setup (WPS) pairing process with WPA2-PSK + WPA3-PSK security enabled is fixed. [NDMS-747]
Dragging and dropping connections in the Internet connection policies now works as expected. [NDW-758]
Selecting and deselecting hosts in Host traffic monitor is improved. [NDW-991]
Ports and VLANs settings are now properly locked on extenders acquired to Wi‑Fi system. [NDW-989]
Highlighting of selected time zone is fixed. [#3644]
The
undefinedstatus of Extender connection in the Wi‑Fi system view is fixed. [NDW-1015]The internet access Schedule for the host can now be edited even when it is blocked manually in the Web Interface. [NDMS-753]
The Speed limit setting and Asymmetric checkbox for unregistered devices are now saved correctly. [NDW-1020]
Wrong DHCP pool calculation and assignment of the DHCP server for newly created segments is fixed. [NDW-1017]
The use NAT setting for Segment page is now saved properly. [NDW-1018]
KeeneticOS 3.4.3
27/5/2020
New
The new WPA3-PSK Fast Transition (FT-SAE) mode is implemented. [NDMS-670, NDW-929]
The independent Pairwise Master Key (PMK) cache storage for Fast Transition and WPA3 is implemented.
Quectel EP06 series LTE Cat6 QMI-type modem module is now supported. [NDMS-718]
Improved
SSTP VPN server compatibility with AnyVPN SSTP Connector application is improved. [NDMS-697]
Initialization of attached USB storage is improved to prevent errors on certain volumes. [NDMS-750]
Fixed
Mounting of disk partitions with UTF-8 encoding in the label is fixed. [NDMS-729]
Group Temporal Key (GTK) re-key process for FT-transitioned Wi‑Fi clients is fixed. [NDMS-709]
Pairwise Master Key PMK-R1 key storage overflow is fixed.
KeeneticOS 3.4.1
13/5/2020
New
Added IEEE 802.11h DFS (Dynamic Frequency Selection) support for Mesh Wi‑Fi System, to prevent interference with satellite and weather radar systems using the same 5 GHz frequency band. In the case of detection of a radar signal, the Keenetic acting as Controller of the Wi‑Fi System will switch to another Wi‑Fi channel for all extenders included in the Wi‑Fi System. [NDMS-632]
Implemented an option to turn off printer polling status. It's helpful for the printer models which do not return correct status. By default, polling status is turned on. [NDMS-209]
printer {name} no status-polling
Implemented upstream speed limit for registered hosts. [NDW-815]
Implemented automatic updating of shared disk resources via the
Change Notificationmechanism of the File and printer sharing (TSMB CIFS) system component. [NDMS-192]
gspca-ov519kernel module added to the OPKG (Open Package) system for KeeneticOS, supporting GSPCA-based webcam devices.
Added the Safe eject button
 for USB storage devices to the USB drives and printers section of the System dashboard. It's best practice to do a proper eject before removing your USB drive from your Keenetic device. [NDW-648]
for USB storage devices to the USB drives and printers section of the System dashboard. It's best practice to do a proper eject before removing your USB drive from your Keenetic device. [NDW-648]Added WebDAV settings in the Private Cloud application page, providing easy management to your WebDAV (Web Distributed Authoring and Versioning) resources on the attached USB drive. [NDW-291]
gspca_sonixjkernel module added to the OPKG (Open Package) system for KeeneticOS, supporting GSPCA based webcam devices.
Implemented PMF (Protected Management Frames) and WPA3-PSK/OWE (Opportunistic Wireless Encryption) for Wireless ISP (WISP) client providing wireless connection to the Internet. [NDMS-498, NDMS-226]
Added the new CLI commands — for safe disconnect and for detailed information display about connected USB drives. [NDMS-510]
system eject {name}— unmount partitions and eject a USB media device cleanly;show media [name]— show information about attached USB media devices.
The SSH server system component of KeeneticOS now supports new modern and robust security algorithms: ChaCha20 symmetric cipher encryption and Poly1305 message authentication code across ed25519 public-key cryptography. [NDMS-516, NDMS-517]
Added the WebDAV (Web Distributed Authoring and Versioning) file server. To access, use https://{hostname}/webdav link. The CLI commands for setting up the WebDAV server are listed below: [NDMS-275]
ip http webdav enable— enable the service;ip http webdav security-level (public | private)— enable or disable access from the Internet;ip http webdav permissive— ignore filesystem ACL;ip http webdav root {directory}— set the root directory;user {name} tag webdav— enable WebDAV access for the user;show ip http webdav— show the current status of the WebDAV server.
Added the SFTP (SSH File Transfer Protocol) file server. The following CLI commands are available for setting up the SFTP server: [NDMS-244]
ip ssh sftp enable— enable the service;ip ssh sftp permissive— ignore filesystem ACL;ip ssh sftp root {directory}— set root directory;user {name} tag sftp— enable SFTP access for the user;show ssh sftp— show the current status.
Added support for the following modems with QMI (Qualcomm MSM Interface) type control interface:
Wireless Backhaul connection shutdown for the Wi‑Fi system controller is now available. It helps to maximize the performance of the Wi‑Fi system if all nodes are connected via wired Ethernet connection. The CLI command is below. [NDMS-314]
mws backhaul shutdown
Added DNS Rebinding protection feature for the
dns-proxyservice of KeeneticOS. [NDMS-437][no] dns-proxy rebind-protect (strict | auto)auto— block IP addresses of thesecurity-level privatesegments (default);strict— block IP addresses from the list: IANA IPv4 Special-Purpose Address Registry.
Implemented
NOTIMPLresponse toIQUERYfor thedns-proxyservice of KeeneticOS, which meansNot Implementederror for DNS requests from network devices. TheIQUERYmethod of performing inverse DNS lookups is made obsolete. [NDMS-465]Added DLNA accessibility for PPP-based VPN servers like PPTP or L2TP/IPsec. It enables the access to DLNA server content via external VPN connection. [NDMS-284]
user {name} tag vpn-dlna— enable DLNA over PPP tag for a certain user account.
Improved
Disabled
dns-proxyrebind protection for the loopback IP address127.0.0.1since it caused some mobile applications to fail. [NDMS-688]Disabled
dns-proxyrebind protection for theplex.directdomain, providing for proper operation of the Plex application. [NDMS-696]Added the 4G/3G network signal level icon
 for USB modems. [NDW-800]
for USB modems. [NDW-800]The Device list page now shows the Ethernet port number for wired devices. [NDW-829]
Gateway and DNS server information is added to the System dashboard page in extender mode. [NDW-872]
Updated to the latest OpenSSL library version 1.1.1g, which fixes the CVE-2020-1967 vulnerability.
Enabled directory listing of WebDAV server resources in a web browser.
Redesigned the Private Cloud tile within the Applications section to provide easy management of WebDAV server, SFTP server and FTP server in one place. [NDW-825]
Updated to the latest OpenSSL library version 1.1.1f, which fixes the CVE-2020-1967 vulnerability.
Multiple improvements to the Internet availability-checking algorithm: [NDMS-600]
Reduced the number of simultaneous connections to conserve network resources, on both Keenetic and external servers;
Enabled sequential polling of test servers, instead of simultaneous polling;
Enabled dynamic polling interval between checks for Internet access.
Added KrØØk/CVE-2019-15126 vulnerability protection against decryption of Wi‑Fi WPA2 traffic. [NDMS-589]
Added randomization for source port of L2TP/IPsec VPN connection, to reduce reconnect time. [NDMS-483]
Updated to the latest OpenSSL library version 1.1.1e, which fixes the CVE-2019-1551 vulnerability.
Implemented advanced host traffic filtering based on MAC address ,to reduce discovery time on the Device lists page of the Web Interface and prevent devices with blocked access to the Internet from any outbound transactions. [NDMS-585, NDMS-586]
Implemented a new feature for
ping-checkservice, which allows restarting a manually-specified interface. [NDMS-569]interface {name} ping-check restart [interface]— enable{interface}restart. Optional{name}argument is omitted (resulting in restarting the same interface) by default;ping-check {name} restart-interface— prior syntax is made obsolete.
The default MTU (Maximum transmission unit) size for WireGuard® VPN connections is set to 1324 bytes to optimize transfer of data through external networks. [NDMS-486]
KeeneticOS service
internet-checkeradds captive portal examination for reliable Internet availability detection. [NDMS-553]Excessive logging of WireGuard® handshake has been reduced to save space for helpful messages in the System log. [NDMS-555]
The new configuration option
upstream-rateallows asymmetric Internet access speed restriction in the upload direction for any giveninterface/host/unknown-host. [NDMS-512]interface traffic-shape rate {rate} [asymmetric {upstream-rate}]ip traffic-shape host {mac} rate {rate} [asymmetric {upstream-rate}]ip traffic-shape unknown-host rate {rate} [asymmetric {upstream-rate}]
Fixed
Fixed Schedule editor operation in mobile browsers. [NDW-738]
Fixed the toggle switch operation for the Private Cloud components on the Applications tile in the dashboard. [NDW-885]
The listing of nested folders now works properly with the Rclone WebDAV client. [NDMS-658]
User can now cancel and clear the host Speed limit configuration for the Registered devices on the Device lists page. [NDW-869]
Internet availability and firmware updates checking are now working properly when AdGuard DNS service is active on the Internet safety page. [NDMS-648]
Removed the
CONFIG_COMPACTIONkernel option to improve memory operations within the task queue handler under heavy loads. [NDMS-423]
Fixed the long reconnection time for backhaul links between Wi‑Fi System nodes. [NDMS-612]
Configuration saving with activated Mode — ICMP echo (ping) for Check the availability of the Internet (Ping Check) section on Web Interface is now working correctly. [NDW-780]
Fixed
SSL_read() failederror on Wi‑Fi system extenders affected by OpenSSL library usage.
Removed IPsec forced rekey for every 20 GBytes of transferred traffic, to improve stability of high load VPN tunnels. [NDMS-483]
Restored client-to-client communication between VPN clients of different VPN servers of KeeneticOS, for example, PPTP and L2TP/IPsec. [NDMS-588]
Traffic counter for incoming and outgoing VPN IPsec tunnels on the Host traffic monitor page of Web Interface. [NDMS-228]
Handling of IP alias for IPIP (IP over IP) with IPsec protection. [NDMS-590]
IPsec VPN tunnel connection now follows a user-defined schedule. [NDMS-594]
Folders with restricted permissions are now appropriately displayed in the File browser. [NDW-285]
Link to KeeneticOS Release notes is now visible on the Updates and component options section of the System setting page. [NDW-739]
Unregistered devices and Multicast traffic tabs of the Host traffic monitor used to disappear on page refresh. [NDW-632]
Listing files and directories of File and printer sharing (TSMB CIFS) application yields an empty response when uninstalled the Folder permissions control component. [NDMS-536]
The printing via File and printer sharing (TSMB CIFS) system component is not possible on the Epson L120 printer due to an invalid printer name in the
OpenPrinterExresponse. [NDMS-381]
The Device lists are now cleared of hosts mistakenly retrieved from OpenVPN connections. [NDMS-567]
Router icon
 display on particular DLNA clients or Smart TV for Media Server component of KeeneticOS. [NDMS-181]
display on particular DLNA clients or Smart TV for Media Server component of KeeneticOS. [NDMS-181]IGMP proxy service deactivation on the
bridge interfaceof the network Segment for the case when both the multicast source and clients are in the same Segment. [NDMS-231]Reset to the default values of Phase 1 — IKE lifetime and Phase 2 — SA (Security Association) lifetime for L2TP/IPsec and Virtual IP VPN connections when some other VPN settings are changed. [NDMS-546]
Folder creation errors while copying folder to WebDAV server on attached USB storage. [NDMS-531]
The reason for
lock precedence violation: IPV6_SUBNETSerror messages in the System log.Network mask parsing in
ip natcommand. It's now possible to use a short notation of IP network mask —ip nat 192.168.1.0/24. [NDMS-552]Private key validation in the Connection settings section of the WireGuard® VPN. [NDW-653]
DNS response with IP address
0.0.0.0is removed from the anti-rebind list of thedns-proxyservice of KeeneticOS because some supported Internet security and content filtering services use such IP address to filter blocked media content and links. [NDMS-528]Updated
pppddaemon responsible for Point-to-Point Protocol (PPP protocol) of KeeneticOS, which fixes the CVE-2020-8597 vulnerability.
Corrected the USB storage status on the Applications section of the System dashboard. [NDW-647]
Fixed one-way RTP (Real-time Transport Protocol) voice communication for VoIP calls via WireGuard VPN tunnel. Now both subscribers can hear each other well. [NDMS-503]
Addressed the shared network discovery issue with the Popcorn PCH-C300 and Dune media players. [NDMS-456]
Fixed the uptime calculation in the
show ip hotspotCLI command. The uptime value is now refreshing properly for all Registered devices. [NDMS-520]
Repaired the task queue corruption related to the Linux kernel
CONFIG_COMPACTIONoption. The change avoids system restart under the heavy system load of applications that use external storage, e.g. Media Server and Download Station. [NDMS-423]WireGuard® VPN tunnel sometimes could not reconnect, after system restart and in some other circumstances. [NDMS-497]
Fixed the System name field's validation to prevent the use of the
spacesymbol. [NDW-620]Fixed the KeenDNS domain name proxy option to preserve the HTTP Host header. [NDMS-490]
Execution of Wireless ACL rules on Wi‑Fi system extenders is now working correctly. [NDMS-398]
A manually configured static IP address on a Wi‑Fi system extender no longer prevents it from connecting to the Internet. [NDMS-89]
Fixed display of Internet connection Status on the System dashboard. [NDW-608]
Repaired the Activate toggle switch on 4G/3G modem page. Toggle is helpful when you need to manage a modem manually. [NDW-615]
PEAP/MS-CHAPv2 authentication now works properly for 802.1x connections. [NDMS-402]
Accelerated WEB Interface response time when thousands of dynamic routes are uploaded to KeeneticOS routing table via OPKG (Open Package) system packages.
Updated the
mini_snmpdsystem service with fixes for the CVE-2020-6058, CVE-2020-6059, CVE-2020-6060 vulnerabilities.