Latest Wi-Fi security: WPA3 and OWE setup
The latest Wi-Fi security algorithms, namely WPA3-PSK, OWE, WPA/WPA2/WPA3-Enterprise, and WPA3-192 Enterprise, have been implemented in KeeneticOS starting with version 3.1.
This feature is supported for all KN-XXXX Keenetic models.
WPA3-192 Enterprise (Suite B) configuration is possible only for Keenetic Giga (KN-1010). Also, WPA3-PSK and OWE protocols for Wireless ISP connections are currently available for this model only.
WPA3-PSK (Wi-Fi Protected Access, developed by the Wi-Fi Alliance and announced in 2018) is a security algorithm that provides data protection in Wi-Fi networks. It pertains to the WPA3-Personal mode, included in the third version of the WPA3 protocol set. The new protocol replaces WPA2, introduced in 2004. The main idea of implementing the new WPA3 protocol is to eliminate conceptual flaws in the WPA2 protocol, particularly to protect against certain types of attack (Key Reinstallation Attacks, KRACK). The WPA3 protocol has a higher level of security than WPA2.
WPA3 allows two modes of operation: WPA3-Personal and WPA3-Enterprise.
WPA3-Personal (WPA3-PSK) provides 128-bit data encryption, and WPA3-Enterprise (Suite B) offers 192-bit data encryption.
OWE (Opportunistic Wireless Encryption) is an encryption method to enhance the security and privacy of users connecting to open (public) Wi-Fi networks.
Please see the following links for more information on WPA3 and OWE security mechanisms: WPA3, SAE, OWE.
Tip
With KeeneticOS versions before 3.4.3, we recommend using the WPA2 network security protocol for better compatibility with roaming enabled. Otherwise, in WPA2+WPA3 mode, devices may prefer WPA3 and thus lose seamless transitions. FT (Fast Transition) support in WPA3 mode is implemented in version 3.4.3 and higher.
WPA3-PSK and OWE configuration is available in the Keenetic web configurator in the 'Wireless Network' settings on the 'Home' page ('My networks and Wi-Fi' menu section). Locate the 'Network protection' drop-down and select the appropriate algorithm for your network.
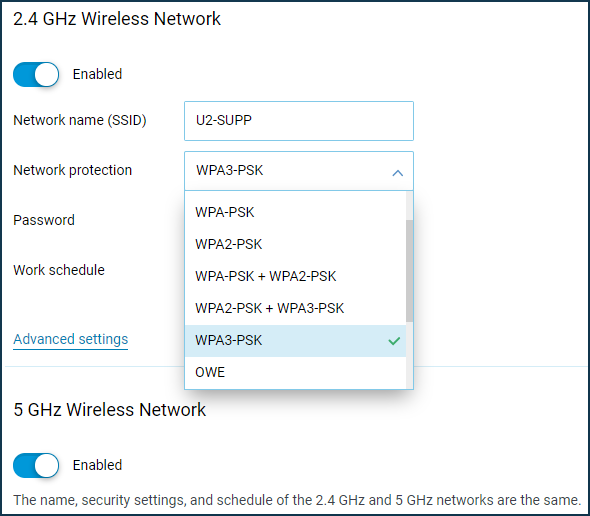
Important
To use the new WPA3-PSK and OWE network protection mechanisms, the connected device must support these algorithms in the driver of its radio module.
When using mixed encryption type 'WPA2+WPA3' with some mobile devices, you may experience speed degradation. For more information, please refer to the article 'What can cause speed degradation on some mobile clients when operating in mixed mode 'WPA2+WPA3'?'
You should only enable WPA2+WPA3 Mixed Mode if you are sure that all your home network devices will operate correctly in this mode.
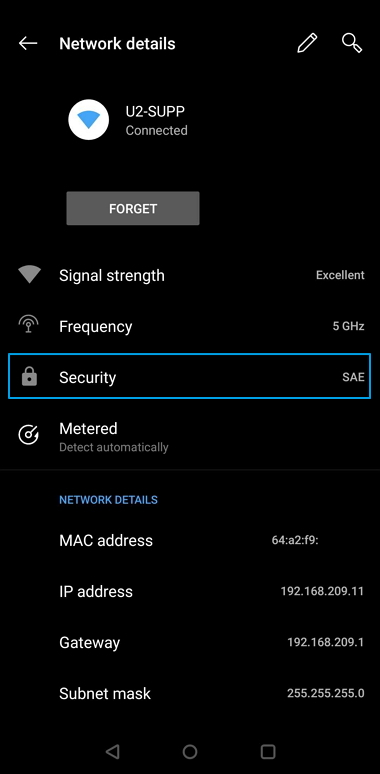
Below are some examples of connection on a Oneplus 6 smartphone (Android 9).
WPA3-PSK network protection (SAE):
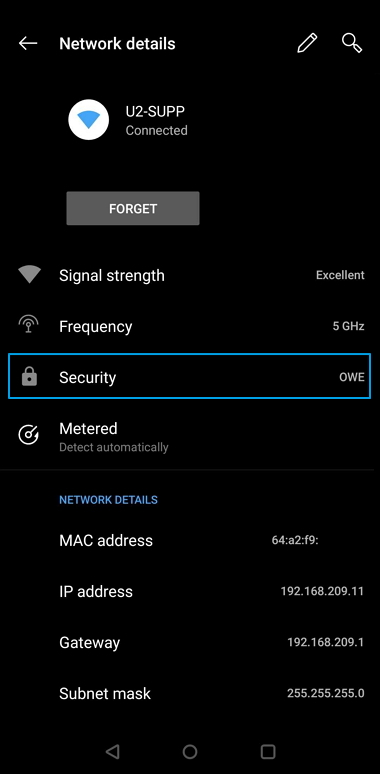
OWE open network protection:
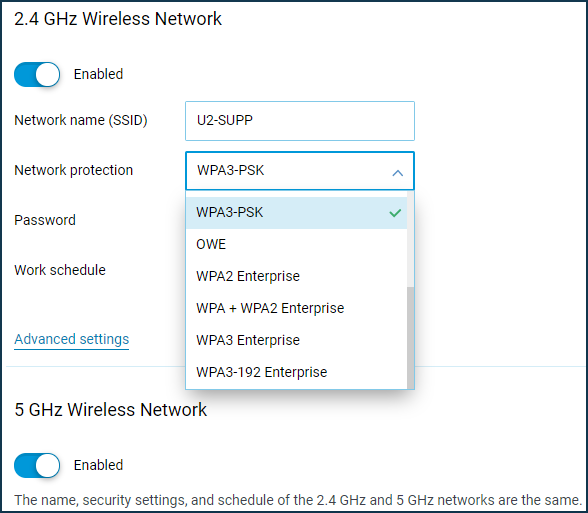
To use the WPA Enterprise protocols, you need to install the 'WPA Enterprise' system component. You can do this on the 'System settings' page by clicking on 'Component options'.

After that, you will be able to configure the WPA Enterprise protocols in the Wi-Fi settings.
Note
WPA3 provides two modes of operation: WPA3-Personal and WPA3-Enterprise.
WPA3-Personal. The most important change in the WPA3 protocol is using a new Simultaneous Authentication of Equals (SAE) method, which provides extra protection against brute-force attacks. SAE is intended to replace the simple PSK (Pre-Shared Key) exchange method used in WPA2. The goal of SAE is to protect the connection establishment process as much as possible from hacker attacks. SAE works under the assumption of device equality. Either side can send a connection request. Then, they start sending their authentication information independently, instead of just exchanging messages one at a time, as with the PSK key exchange method. SAE uses a special variant of establishing the connection (dragonfly handshake), which uses cryptography to prevent an attacker from guessing the password.
In addition to the above, SAE uses perfect forward secrecy (PFS) for an additional security enhancement that the PSK did not have. Let's say an attacker gets access to encrypted data that a router sends and receives from the Internet. Previously, an attacker could save this data and then, if the password was successfully picked, decrypt it. With SAE, a new encryption password is set with each new connection, and if a hacker penetrates the network at some point, he can only steal the password from the data sent after that point.
The SAE authentication method is described in detail in the IEEE 802.11-2016 standard.
WPA3-Enterprise. This operating mode is intended for use in institutions with the highest demands on information security and confidentiality. WPA3-Enterprise (Suite B) provides 192-bit data encryption.
OWE (Opportunistic Wireless Encryption) is an extension of the IEEE 802.11 standard, similar to SAE. OWE secures data transmitted over an unsecured network by encrypting it. Users are not required to take any extra steps or enter passwords to connect to the network.
Many attacks that occur on an open network are classified as passive. When many clients connect to a network, an attacker can collect a great deal of data simply by filtering the information that passes by.
OWE uses opportunistic encryption, defined in RFC 8110, to protect against passive eavesdropping. It also prevents packet injection attacks, where an attacker tries to disrupt the network by creating and transmitting special data packets that look like part of regular network operation.