KeeneticOS 3.5
KeeneticOS 3.5.6
12/12/2020
Improved
Improved security: The OpenSSL library is updated to version 1.1.1i. It fixes the CVE-2020-1971 vulnerability.
KeeneticOS 3.5.5
9/12/2020
Fixed
The bug in domain name processing is fixed. Now clients of your home network can correctly resolve the domain name of the Keenetic device booked with KeenDNS service. [NDMS-1250]
KeeneticOS 3.5.4
26/11/2020
Fixed
The System dashboard used to display the wrong MAC address for the PPPoE Internet connections with spoofed MAC address. [NDW-1583]
KeeneticOS 3.5.3
20/11/2020
New
There are no changes for Keenetic City(KN-1510).
Improved
Years ago Reset button was defined to perform two functions: Long pressing for 10 seconds to return device to factory defaults and quick pressing to restart device. This dualism introduced a number of issues to Keenetic customers as they can not visually distinguish between the two cases. From now on Reset button is exclusively for return to factory defaults. [NDMS-1141]
Fixed
Incorrect wireless back-haul connection speed and up-link node were displayed in the extender list of the Wi‑Fi system. [NDMS-1154]
The traffic acounting for unregistered hosts is improved. [NDMS-1093]
The arrow sign in the auto-generated descriptions of UPnP forwarding rules is now displayed correctly. [NDW-1501]
KeeneticOS 3.5.2
21/10/2020
Fixed
The performance of the Traffic shaper component is improved. [NDMS-1090]
The Mesh Wi‑Fi system Extender device's best path selection algorithm for wireless back-haul connection is improved. This change now provides greater stability and performance of the Mesh Wi‑Fi system's nodes interconnections. [NDMS-1120]
The port forwarding rule setting in the web interface is restored. The rule for the combination of TCP and UDP protocols can now be properly added on the Port forwarding page in the web interface. [NDW-1436]
The Mesh Wi‑Fi system Controller device now correctly removes the Extender device's default static IP address
192.168.1.3from the Members list view once the new address is acquired via DHCP. [NDMS-1097]
KeeneticOS 3.5.1
15/10/2020
New
There are no changes for Keenetic City(KN-1510).
KeeneticOS 3.5 Beta 7
4/10/2020
New
There are no changes for Keenetic City(KN-1510).
Improved
Improved security: The OpenSSL library is updated to version 1.1.1h
Fixed
A new Firewall rule will now be, correctly, added to the top of the rules list in the web interface. [NDW-1413]
The Connection names on the Internet safety page are now correctly displayed in the language configured for the web interface. [NDW-1397]
KeeneticOS 3.5 Beta 6
29/09/2020
New
There are no changes for Keenetic City(KN-1510).
Fixed
The case when a remote VPN client connected to the IKEv2 server running on the Keenetic can't access the Internet is now fixed. [NDMS-1019]
KeeneticOS 3.5 Beta 4
13/09/2020
Improved
There are no changes for Keenetic City(KN-1510).
Fixed
The non-applicable No IP address option is removed from the advanced settings of the VPN connections in the Other connections section of the Web Interface. [NDW-1351]
The list of the available Connections for the Internet Safety - DNS Servers setting of the Web Interface is fixed : only
publicinterfaces can be chosen. [NDW-1352]
KeeneticOS 3.5 Beta 3
6/09/2020
Fixed
Filtering of Ethernet frames without VLAN tags, received on the WAN port configured in trunk mode, is fixed. It blocks untagged data leakage from the Internet provider into the home network. [NDMS-899]
The removal of the restriction on open wireless bands is now working properly. Selecting back the Both bands setting restores the default behaviour. This configuration option allows the limiting of the connection of a dual band wi-fi client to a particular wireless band only: 2.4 or 5 GHz. The setting works for both a standalone device and / or a Wi‑Fi system with multiple nodes. [NDMS-763, NDMS-866]
KeeneticOS 3.5 Beta 2
6/09/2020
New
There are no changes for Keenetic City(KN-1510).
Improved
The internal logic of the IGMP snooping component is improved for the scenario when several multicast clients are connected to the LAN port of the device via a single external Ethernet switch or several daisy-chained Ethernet switches. [NDMS-981]
Fixed
Fixed the handling of multiple subscriptions to a multicast group on different Ethernet ports of a device operating in Extender mode. [NDMS-1002]
KeeneticOS 3.5 Beta 1
27/08/2020
New
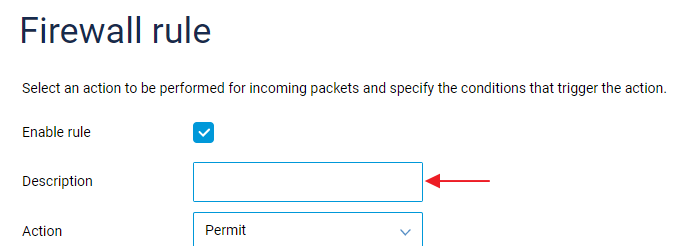
Rules enrichment: A description field has been added to the firewall rules control. [NDMS-939, NDW-1302]
New in NetFlow: The NetFlow Monitor system component is now enabled to set the version of flow records sent towards flow collectors. Specifically, NetFlow versions 5, 9 and 10 (IPFIX) are supported. Configuration is available from the command line interface only. [NDMS-631]
ip flow-export version {version}
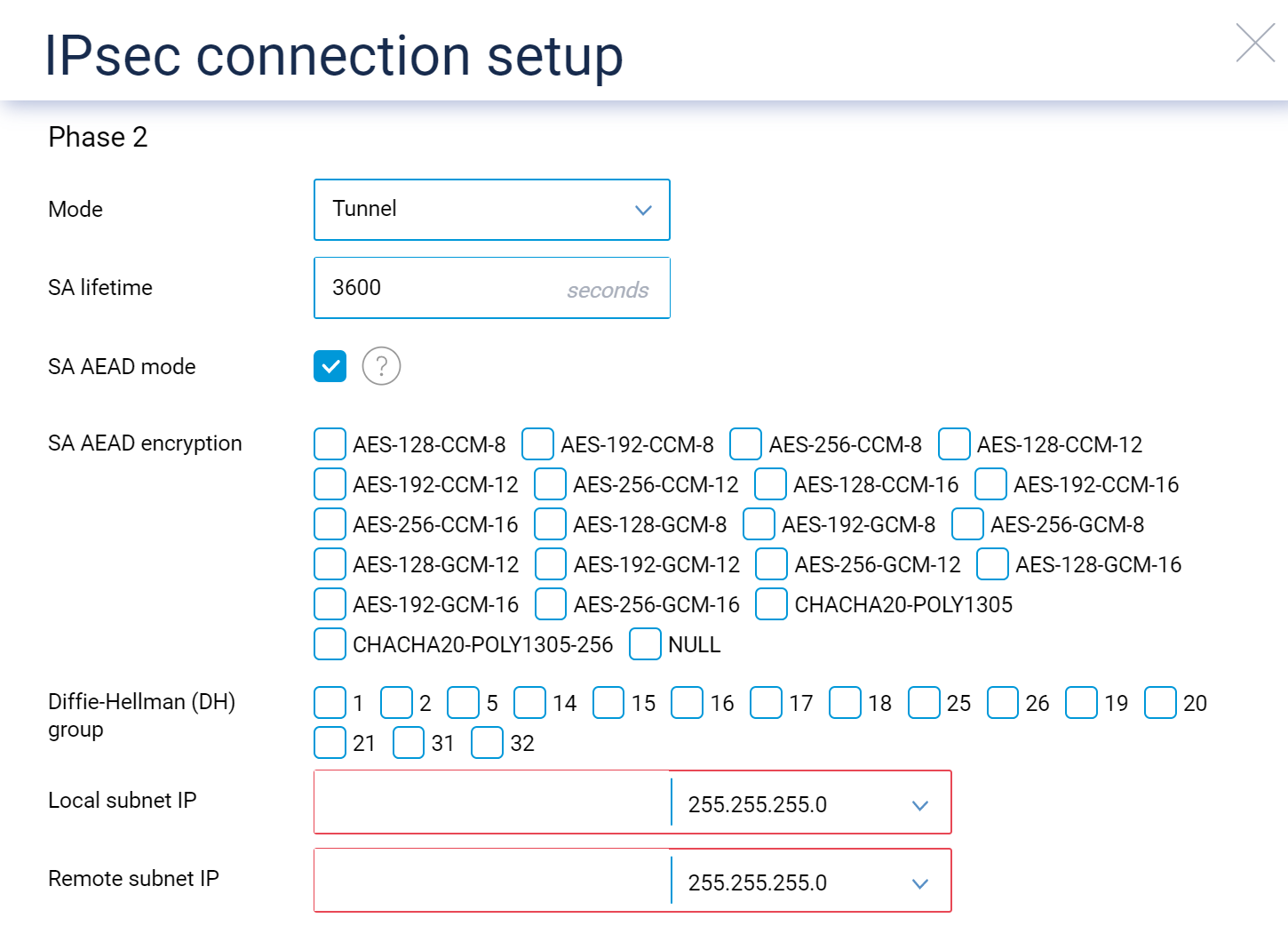
Better IPSec security: The IPsec VPN system component now has the latest and greatest security options for making your IPsec VPN tunelling as safe as possible. IPsec connections now support:
the AES-CTR encryption algorithm;
the AES-CCM, AES-GCM and CHACHA20-POLY1305 combined-mode/AEAD cipher algorithms;
new elliptic-curve Diffie–Hellman groups, including
ECP 192/256/384/521andx25519/x448.
[WEB-4059]
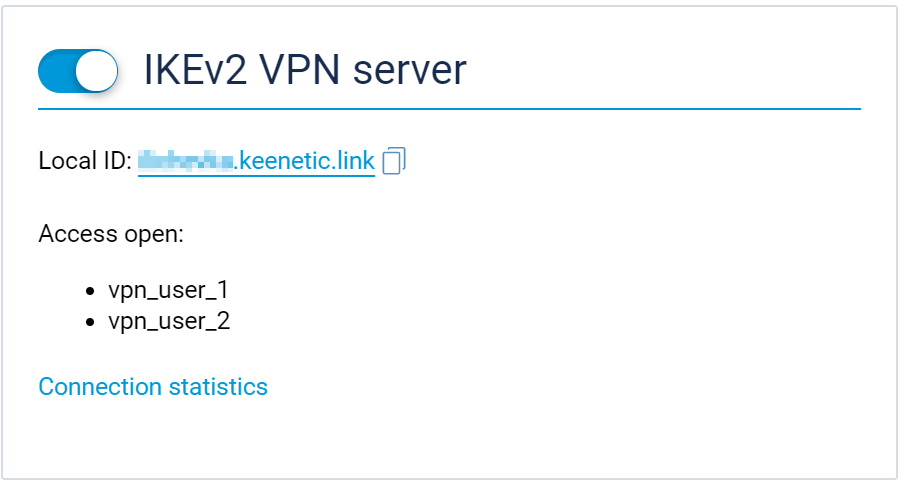
New, up-to-the-minute, security: The IKEv2 VPN server application is now live. IKEv2 stands for Internet Key Exchange, version 2 (this VPN protocol is also referred to as IKEv2/IPsec, but as IKEv2 is never implemented without the IPsec encryption layer, it is generally shortened to just IKEv2). IKEv2 is one of the newest security protocols, with high speed, and with VPN clients available for all desktop and mobile platforms. [NDW-1208]
Enriched KeenDNS service: An advanced configuration option is now available for users of the KeenDNS web applications feature — the real IP address of a remote client can be presented to the web application, instead of the Keenetic router's IP address.
ip http proxy {name} x-real-ip
Performance improvement: Active queue management is now enabled in the traffic control module, to combat bufferbloat and reduce network latency. [NDMS-707]
Interface extension: It is now possible to integrate the Web Interface of your Keenetic into an interface of another system (for example a smart home automation system) using the
iFrameoption. For security reasons this option is disabled by default. Use the following CLI command to enable it. AniFrameis an inline frame used inside a webpage to load another HTML document inside it.ip http x-frame-options {x-frame-options}
The single-band Wi‑Fi Keenetic models can now acquire dual-band Wi‑Fi extenders to Wi‑Fi system and deploy 2.4 GHz back-haul connections between Wi‑Fi System nodes. [NDMS-819]
The new QoS (Quality of Service) mechanism based on service class packet flows is implemented. QoS allows provision of different priorities to different applications, devices, or data flows, to guarantee a certain level of performance. [NDMS-722]
The CLI command to assign service class(es) to registered devices is implemented according to a new QoS mechanism. Traffic from devices with service class 1 are processed with the highest priority. If a service class is not set (by default), the traffic is processed with priority between class 5 and class 6. [NDMS-771]:
ip hotspot host {mac} service-class {1-6}
The new IKEv1 IPsec VPN connection client is now available. Go to the VPN connections section of the Other connections menu to configure it. [NDW-1025]
The list of languages of the Web Interface is added to the system components. It is now possible to install only necessary languages and remove any unnecessary, to save flash memory for other applications. [NDW-1046]
The Inbound management access control setting in the Web Interface of the Wi‑Fi system controller will apply to all Wi‑Fi system extenders. [NDW-1006]
The new Wi‑Fi bands open for connection option is implemented. This configuration option allows the limiting of the connection of a dual band wi-fi client to a particular wireless band only: 2.4 or 5 GHz. The setting works for both a standalone device and a Wi‑Fi system with multiple nodes. [NDW-987]
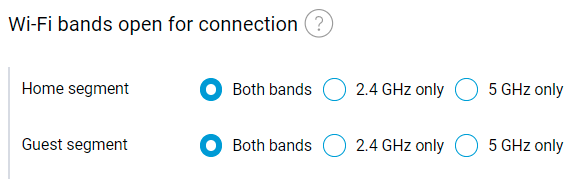
The new IPsec IKEv2 VPN client is now available as a system component in the Network functions category of KeeneticOS. This type of VPN is very popular among VPN service providers like NordVPN, SecureVPN and others. [NDMS-625, NDW-949]
The new IPsec IKEv2 Virtual-IP VPN server, using a Let's Encrypt® certificate, is now available. [NDMS-703]
Note
The IPsec IKEv2 Virtual-IP VPN server allows authorized users to connect to your home network resources over the Internet, using a secure and robust tunneling protocol.
The IKEv2 client is available out-of-the-box in modern releases of Windows, MacOS and iOS operating systems, and most Linux distributions.
crypto virtual-ip-server-ikev2
The new Application-layer gateway (ALG) for ESP system component is added. This component provides customized NAT traversal filters to support address translation for the ESP protocol. It's a kind of IPsec pass-through feature, which helps to pass ESP packets of IPsec connection through the Keenetic router. [NDMS-683]
ip esp alg enable
The new WPA3-PSK Fast Transition (FT-SAE) mode is implemented. [NDMS-670, NDW-929]
Note
WPA3-PSK is a new and much stronger standard of Wi‑Fi security. SAE is Simultaneous Authentication of Equals, a password-based authentication and key establishment protocol initially introduced in IEEE 802.11s for mesh networks. Fast Transition is a standard for Wi‑Fi roaming between Wi‑Fi System nodes.
The independent Pairwise Master Key (PMK) cache storage for Fast Transition and WPA3 is implemented.
The new Command Line Interface (CLI) command for fixing dual band Wi‑Fi clients to a 2.4 or 5 GHz band is implemented. [NDMS-506]
interface {Bridge} mac band {mac} (0|1)— allow{mac}associations to 2.4GHz (0) or 5GHz (1) only, and ignore any request on the other band
Support for Cloudflare DNS content filtering service is implemented in the Command Line Interface (CLI). There are three levels of protection:
standard,malware,family. [NDMS-617]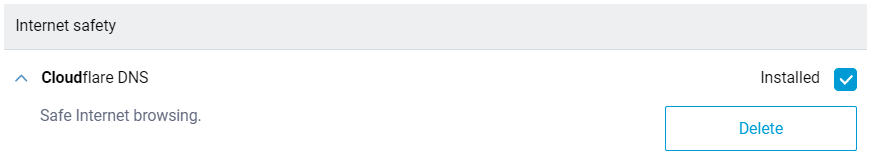
cloudflare-dns check-availabilitycloudflare-dns assign {mac} (standard | malware | family)cloudflare-dns enableshow cloudflare-dns availabilityshow cloudflare-dns profiles
The randomized HTTP session cookie name is implemented. It enhances concurrent access to the Web Interface of customer network devices via port Forwarding. [NDMS-596]
Improved
Security enhancement: A new network protection mode WPA2 + WPA3 Enterprise is now available, delivering enhanced security. The WPA Enterprise modes are designed for use in distributed networks and require a RADIUS authentication server. [NDW-1299]
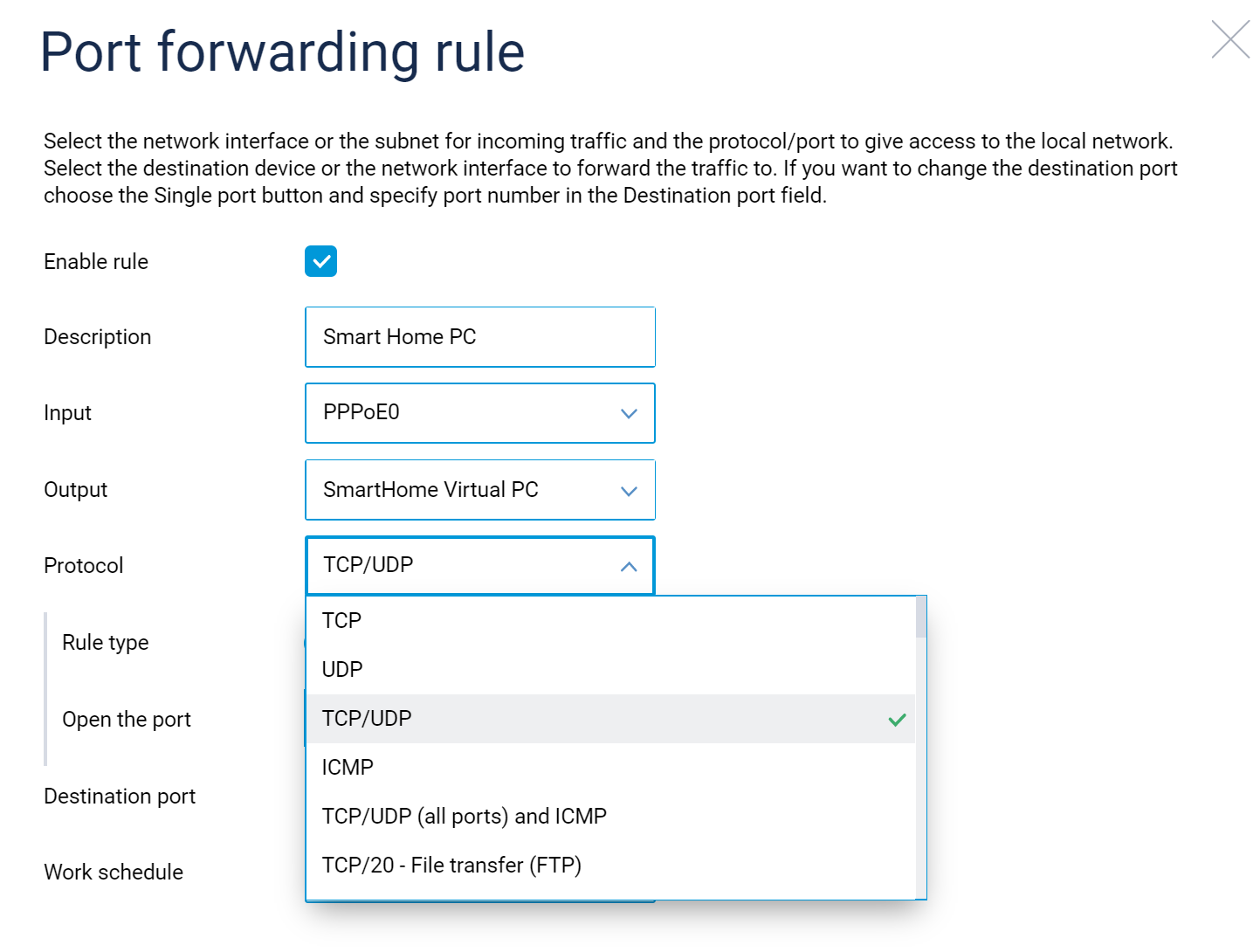
Configuration enriched: The Port forwarding rule form now has dual TCP/UDP protocol options for your greater convenience in configuring access to the services on your local network from the Internet. [NDW-1241, NDMS-909]
Major security upgrade: Access from the Internet to web applications running on a home network via your registered KeenDNS domain name has been given a substantial security upgrade. If your application runs the HTTPS protocol, you can now select this protocol type in the configuration settings. Most importantly, the Allow access from the Internet configuration option is now independent from any decision you might make to allow remote access to the Web Interface of your Keenetic itself, as configured at the Management > Users and access > Remote access page. [NDMS-927, NDMS-215, NDW-1242, NDW-1237]
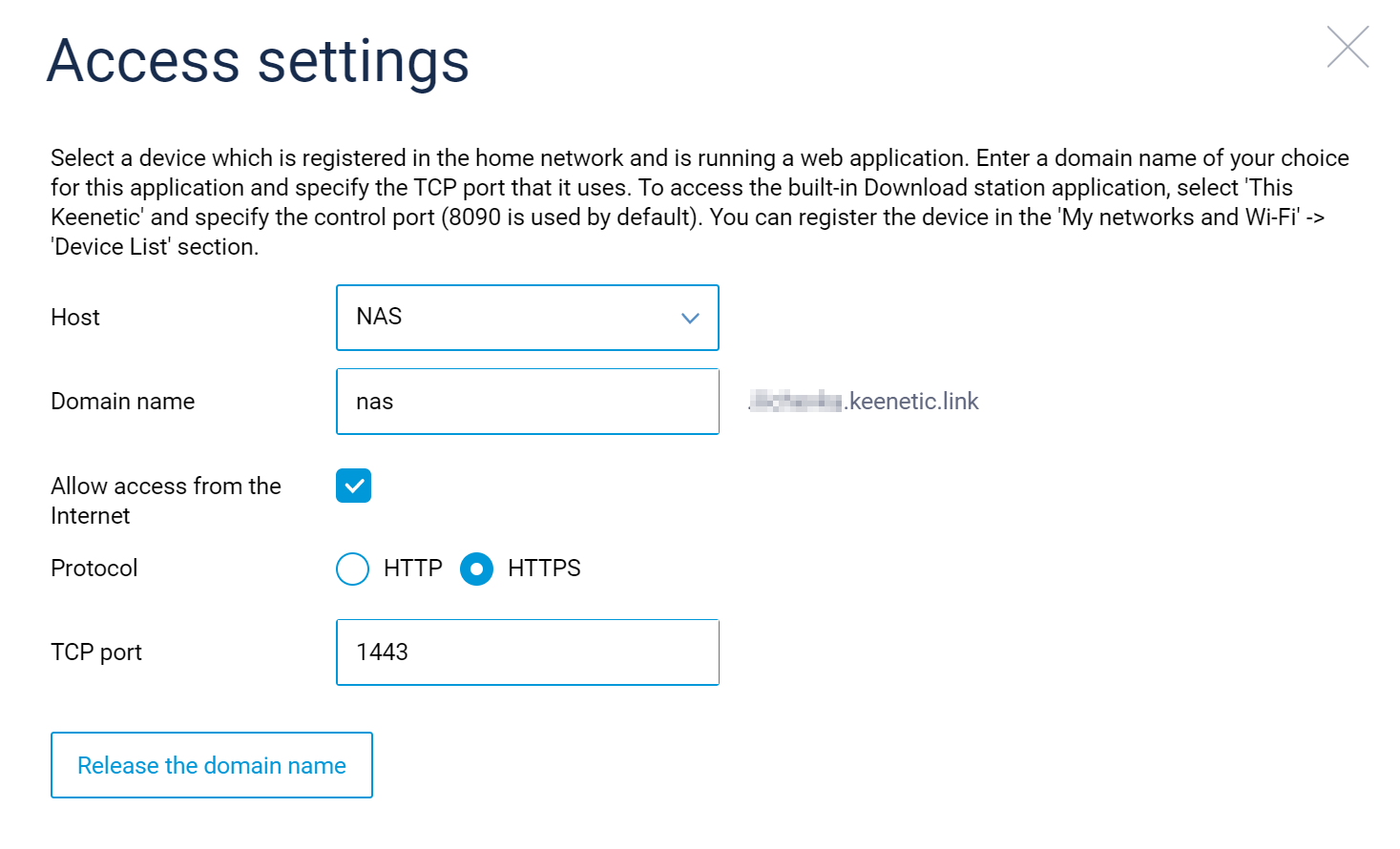
ip http proxy {name} security-level (public | private)ip http proxy {name} upstream (http | https) (‹mac› | ‹ip› | ‹fqdn›) [‹port›]
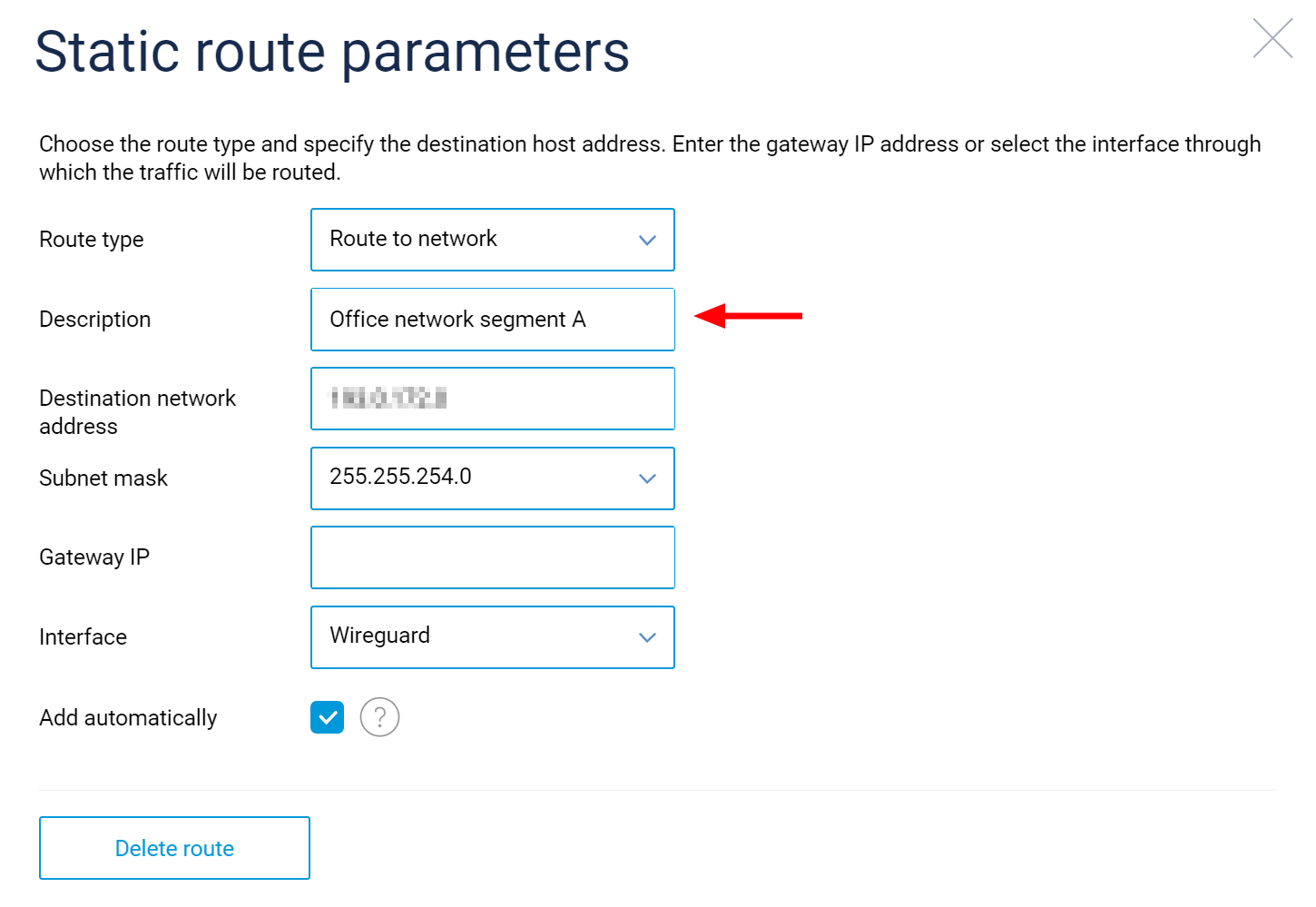
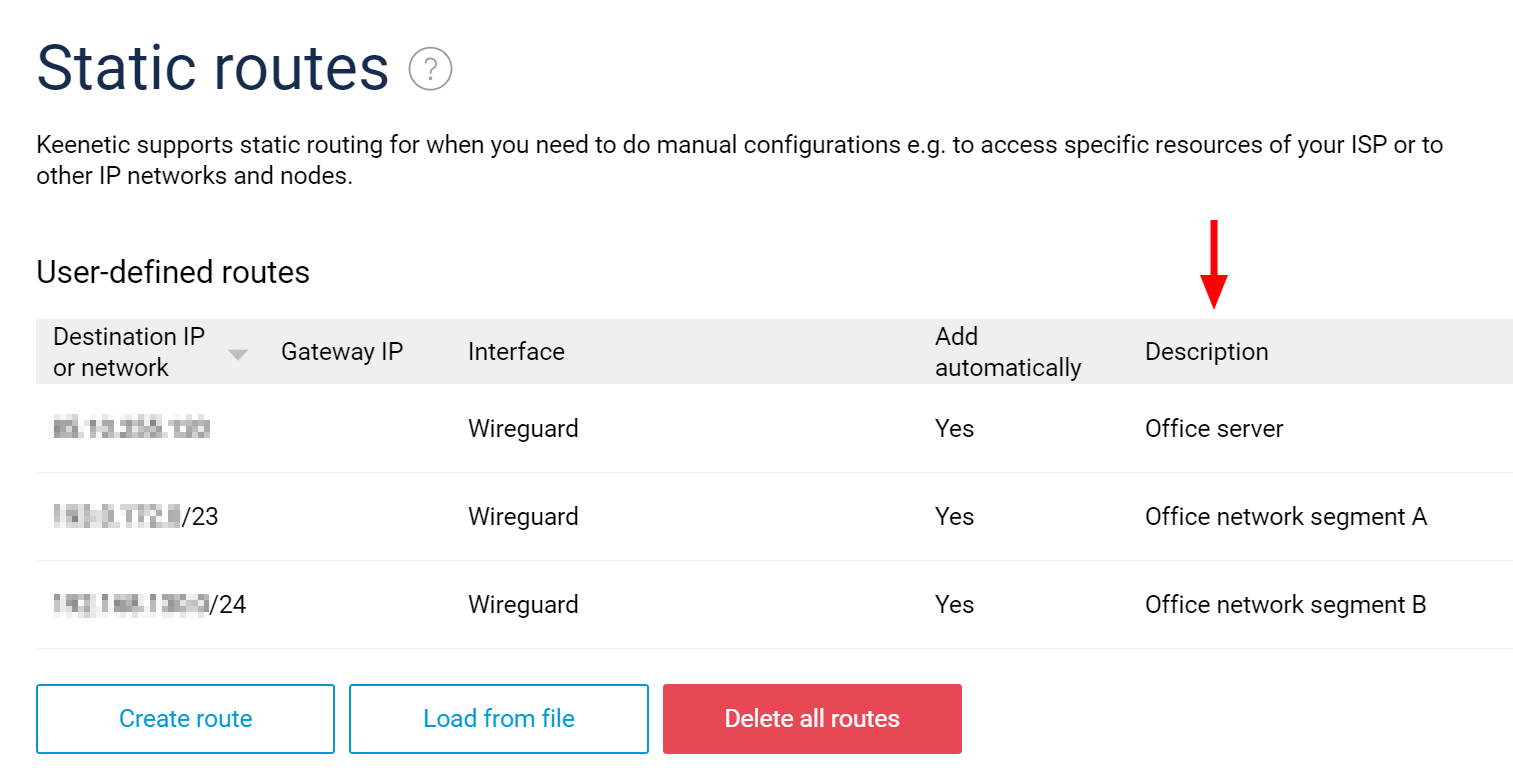
Network rules note facility: In the Network Rules > Routing section there is now a way to describe the purpose of a particular static route entry. A Description field is added to the Static route parameters form and User-defined routes table. Further, for your greater convenience, you can sort the table by clicking any column header row, including Description. [NDMS-911, NDW-1231]
Security efficiency: The IPsec encryption algorithms AES-CTR, AES-CCM and AES-GCM are now partially hardware-accelerated on devices equipped with the AES Crypto Engine.
Traffic shaping improvements: When a traffic shaping rule is applied to a host in your network, or a network segment, it is now live almost instantly. Remember that the maximum Internet access speed can be shaped independently in each of the upload and download directions. [NDMS-898]
Remote web application access: KeenDNS allows you to enable access from the Internet to web applications running on your network. If your web application runs on HTTPS protocol, the new
httpsoption will help to set it up. [NDMS-215]ip http proxy {name} upstream (http | https) ({mac} | {ip} | {fqdn}) [{port}]
The WireGuard® VPN system component is updated to version 1.0.20200623. WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography.
The new firmware signing certificate is deployed to the cloud infrastructure. Previously saved firmware files can be uploaded using the TFTP recovery mode only. [NDMS-828]
The Ethernet MAC table reading operation is optimized. The Device lists page loads much faster if you have many devices connected to your network. [NDMS-488]
The procedures of KeenDNS service SSL-certificate revocation and renewal are improved. [NDMS-49]
In case of Wireless ACL using Blacklist access control mode, newly registered devices will no longer be automatically added to the blacklist. [NDW-1108]
For the purpose of Keenetic firmware image size optimization, the maximum number of installed languages in the system is limited to three. [NDW-1127]
STP (Spanning Tree Protocol) is now disabled on the Wi‑Fi System controller if there are no systems members acquired. [NDMS-693]
The colon symbol
:in HTTP Cookie headers is now supported. It allows the support of non-RFC based Web interfaces of network devices which are available via the Port forwarding setting. [NDMS-779]The new logic of the Application-layer gateway (ALG) for SIP protocol component with
Media Description > Media Type: Applicationis added. [NDMS-680]
Selecting and deselecting hosts in Host traffic monitor is improved. [NDW-991]
The Remote web interface connections setting from the Users and access management section is now propagated from the Wi‑Fi system controller to all extenders for better remote management control. [NDMS-727]
The Cloudflare DNS internet filtering service is added to the Web Interface. The user can select Service > Cloudflare DNS protection policy on the Internet safety page for each registered host, and Default policy for unregistered hosts. [NDW-971]
Connection statistics for the IPsec Virtual-IP VPN server are implemented, with traffic and time accounting for each incoming VPN connection. [NDMS-685]
SSTP VPN server compatibility with AnyVPN SSTP Connector application is improved. [NDMS-697]
Fixed
WPA + WPA2 Enterprise/WPA2 Enterprise/WPA2 + WPA3 Enterprise network protection modes are now working properly for hidden network names (SSIDs). [NDMS-929]
Dashboard stability: A fix has been implemented for a bug which sometimes caused the System Dashboard view to crash when the Cloud-based remote control and KeenDNS system component was not installed. [NDW-1247]
Cleaner logs: After an unsuccessful attempt to establish SSL session(s) during SSTP VPN connection initiation, the
do_page_fault() SIGSEGVerror was appearing in the system log file - the problem causing this error has been fixed. [NDMS-933]
Even better Help: Context help signs
 are now perfectly aligned across the web interface. Clicking the context help sign lists the relevant topics from the Keenetic online user manual. [NDW-1223]
are now perfectly aligned across the web interface. Clicking the context help sign lists the relevant topics from the Keenetic online user manual. [NDW-1223]
An IPsec performance degradation issue introduced with the addition of ESP ALG was fixed. [NDMS-897]
Initial setup wizard could not start after restoring factory settings on device. [NDW-1198]
Device list cleaning: Occasionally, registered hosts appeared twice on the Registered devices list - this has now been fixed. [NDMS-884]
Better traffic counting: Part of the traffic was sometimes counted incorrectly in the Host Traffic Monitor as coming from unregistered hosts. The Host Traffic Monitor is a useful tool, valued by both consumer and small business users, that tracks Internet traffic consumption by devices in your home or office. [NDMS-738, NDMS-737]
Connectivity: A few Wi‑Fi clients had trouble connecting to a Keenetic Wi‑Fi network configured in WPA2-PSK + WPA3-PSK mixed mode. [NDMS-858]
More powerful remote activation: Sending a Wake-on-LAN magic packet from a remote location over the Internet to turn on a device in the local network did not work for network segments with Connection policy for unregistered devices set to No Internet access - this is now resolved. [NDMS-844]
Acquisition of a Keenetic in extender mode into an existing Wi‑Fi system now works without errors. [NDMS-857]
The incorrect Wi‑Fi LED indication of hardware-accelerated network traffic is fixed. Now the Wi‑Fi LED indicator blinks as intended.
The wrong selection of Web Interface languages is fixed. Up to three languages can be installed at the same time. [NDW-1147]
Minor formatting issues across the Web Interface are fixed. [NDW-1101, NDW-1094, NDW-1058]
The situation when a Wi‑Fi Extender can't establish a back-haul connection to the Wi‑Fi Controller is fixed. [NDMS-804]
Wireless ISP (WISP) connection now works properly when Backhaul connection of Wi-FI System is in use. [NDMS-615]
The client's VPN connections list of the VPN server connection statistics page in the multiple sign-in mode is fixed. Now all active VPN connections are visible. [NDW-1060]
The lost tool-tip over registered devices Online, Offline, Blocked is returned to its previous place on the Device lists page. [NDW-1056]
The incorrect code-style tool-tip of the WireGuard connection is fixed. Now it shows the correct status of the connection. [NDW-1055]
The Domain name page formatting and help sign
 position are fixed. [NDW-1057]
position are fixed. [NDW-1057] The style of the text is slightly changed to fill the available width value of the select box in Web Interface. [NDW-1053]
The incorrect empty list of Extenders in Wi‑Fi System is fixed. It occurred if one of Extenders was in offline mode. [NDW-1044]
The evaluation of nesting of bridged interfaces is corrected. Currently, the configuration order of
interface bridge[x]interfaces is processed rightly. [NDMS-765]
An error in the Wi‑Fi Protected Setup (WPS) pairing process with WPA2-PSK + WPA3-PSK security enabled is fixed. [NDMS-747]
The internet access Schedule for the host can now be edited even when it is blocked manually in the Web Interface. [NDMS-753]
Tooltip formatting for a list of VPN connections in Other connections section is fixed. [NDW-1019]
The
undefinedstatus of Extender connection in the Wi‑Fi system view is fixed. [NDW-1015]The Speed limit setting and Asymmetric checkbox for unregistered devices are now saved correctly. [NDW-1020]
Wrong DHCP pool calculation and assignment of the DHCP server for newly created segments is fixed. [NDW-1017]
The use NAT setting for Segment page is now saved properly. [NDW-1018]
Dragging and dropping connections in the Internet connection policies now works as expected. [NDW-758]
Ports and VLANs settings are now properly locked on extenders acquired to Wi‑Fi system. [NDW-989]
Highlighting of selected time zone is fixed. [#3644]
Pairwise Master Key PMK-R1 key storage overflow is fixed.
The placement of the Delete schedule button is changed to provide better formatting. [NDW-963]
The incorrect IP subnet validation in the IP setting of the network segment is fixed in the Web Interface. [NDW-943]